Security Policy Management made smarter
Boost efficiency, increase agility, and dramatically cut costs with smart automation for network security policy management.
Outdated, manual, and error-prone network security policy management processes can’t keep pace with your organization’s complex hybrid estate of firewalls and networked devices.
Smart automation transforms your network security policy management, reduces security misconfiguration errors, eliminates the risks posed by weak security controls, and dramatically improves process efficiency.

Smarter network visibility
Siloed data makes it impossible to see what you need to protect across your hybrid network. A smarter approach is to aggregate this data into a single dynamic security model.
See how to automatically create a digital twin of your network to reveal the entire attack surface and understand the security controls, assets, vulnerabilities, threats, and network topology of your hybrid network.
Smarter access path analysis
Access changes without the necessary context expose your organization to serious risk. A smarter approach understands where a change to access exposes a vulnerable asset or opens up an attack path.
Learn how to automatically analyze all access paths, sandbox firewall rule changes to assess their impact, and reduce the risk of introducing weak security controls into the real network.

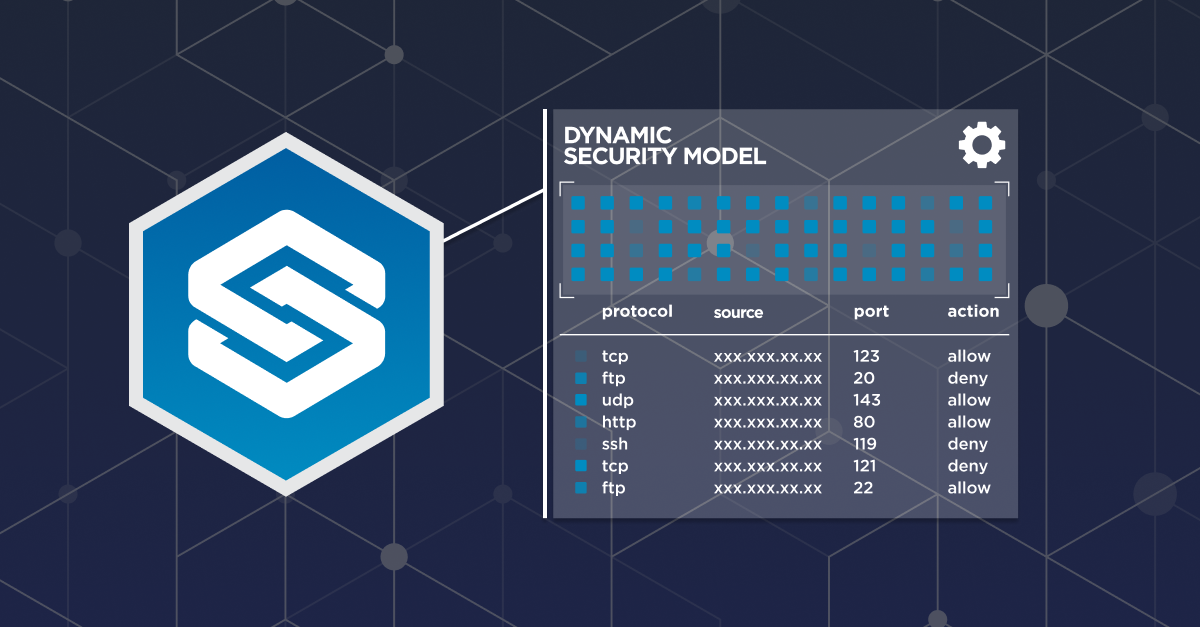
Smarter change management
Manual change management is time-consuming and error-prone. A smarter approach uses automated workflows to drive firewall rule changes from initial request, through data gathering and risk assessment, to provisioning and final verification.
Find out how automation reduces the risk of misconfigurations and weak controls, ensures all the relevant stakeholders are engaged, and drives business forward.
Smarter policy compliance
Achieving compliance is time-consuming and burdens skilled resources. A smarter approach uses automation to ensure firewall configuration and access rules comply with best practices and to orchestrate rule recertification for ongoing compliance.
Discover how to reduce mundane and repetitive manual processes, keep the rule base relevant, and ensure the organization is continuously compliant and audit-ready.

Learn more about Network Security Policy Management
The complexities of today’s hybrid environments are hard to manage. Having a strong security policy helps minimize risk and better protect the organization.
Automation policies leave the team free to focus on core business activities while routine, manual, and mundane tasks are automatically, securely, and safely executed without intervention.
Learn how to improve network security & efficiency, and reduce costs using smart automation.
Leverage automation to combat skill shortages, streamline tasks, simplify network security policy compliance, and identify vulnerability exposures