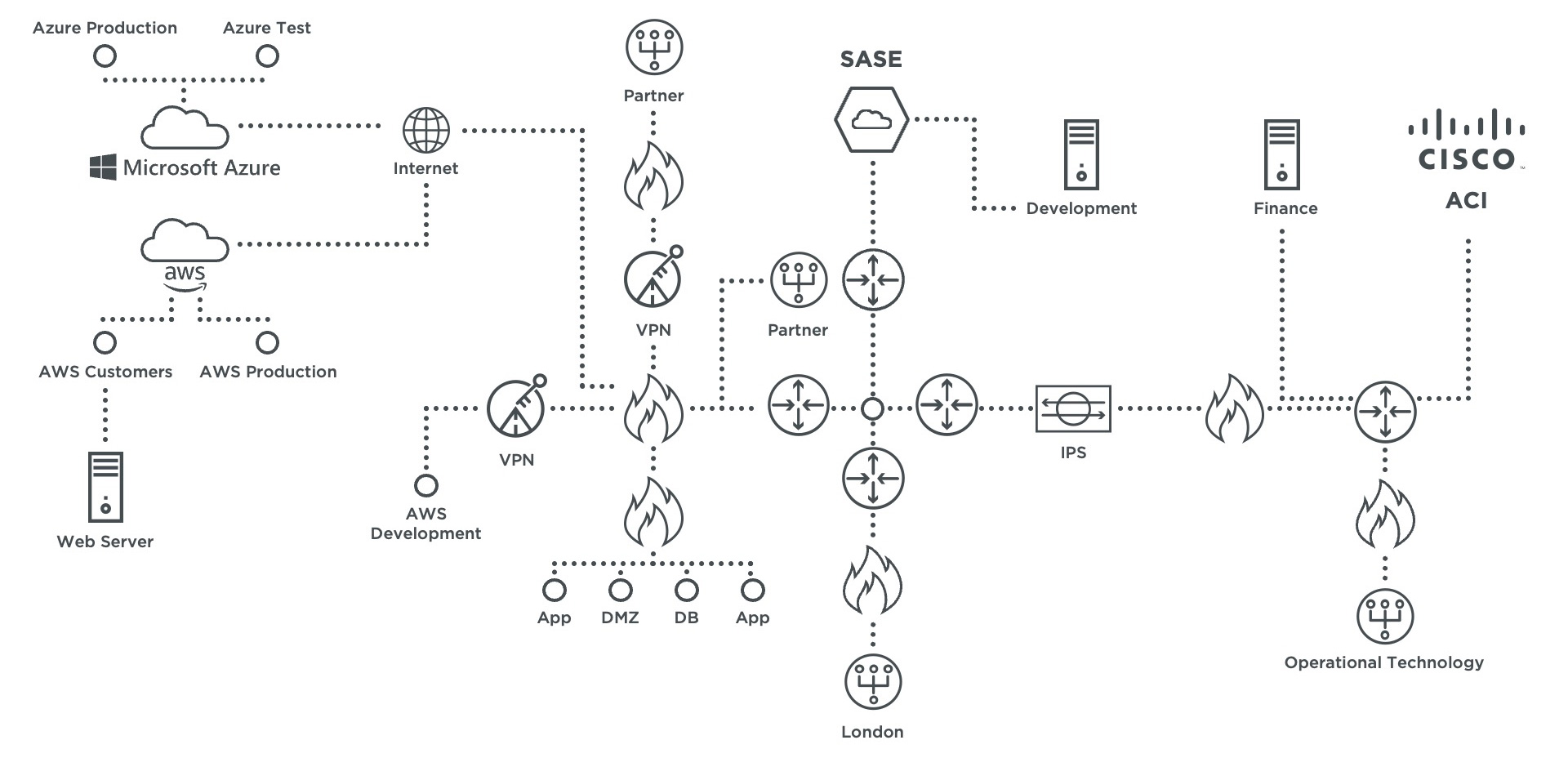
In today’s hybrid networks, security policies need to be managed across large and complex on–premises and multi–cloud networks comprised of security devices from a variety of vendors. With literally tens of thousands of firewall rules across thousands of different devices, changes are rapid and complicated. Managing these networks using manual methods quickly becomes impossible, and can cause disruptive errors and outages, as well as security risks and compliance violations.
To overcome these challenges, you’ve got to start with unified visibility across the entire network. Only then will tools and teams be able to understand risk, maintain continuous compliance and identify, prioritize and provision needed security changes.
The integrated Cisco ACI and Skybox Security solution
With the integration of Skybox Security into the Cisco ACI architecture, customers can rapidly achieve the full potential of their ACI deployment. Integration features include:
- Network visibility and security analysis across the ACI data model, other virtual and cloud environments, on–prem IT and even operational technology (OT) networks.
- Network and security access auditing of the ACI policy model.
- Integrated analysis and change control of on–prem, cloud and hybrid environments.
Skybox Security complements the Cisco ACI architecture by extending and enhancing its policy–based automation to all security devices across the enterprise network, both inside and outside the data center. With Skybox Security’s model–driven visibility and unified policy management capabilities, customers can quickly:
- Assess and reduce risk.
- Ensure continuous compliance.
- Maintain a strong security posture across their entire hybrid network.
Skybox imports the ACI configuration from the Cisco Application Infrastructure Controller (APIC) and creates a virtual model of the fabric layer, including bridge domains and virtual routers as well as the access control layer, EPGs and contracts. Skybox supports APIC versions 3.x to 5.x using REST APIs. Data from Cisco ACI servers can be collected using Cloud & Virtualization – Cisco ACI Collection tasks.