Vulnerability Control
Make your scanning program 10x more effective, reduce critical and high-severity vulnerabilities by 80%, and slash remediation times from months to hours.
Watch a Demo: See how Skybox Vulnerability and Threat Management reduces risk.
Featured Webinar: Vulnerability Management: How to avoid the 3 biggest mistakes.
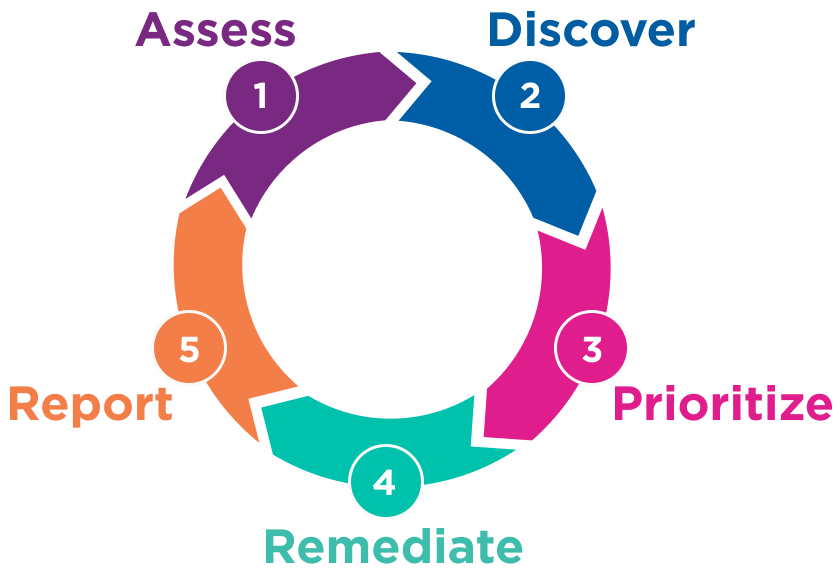
Build out a modern vulnerability and threat management program:
Attackers are looking to exploit vulnerabilities in your IT estate. Orchestrate your response and close them out, with the Skybox Vulnerability and Threat Management solution:
- Assess the attack surface and discover every vulnerability.
- Prioritize according to risk and select from a choice of remediations.
- Monitor and report to stakeholders across the organization.
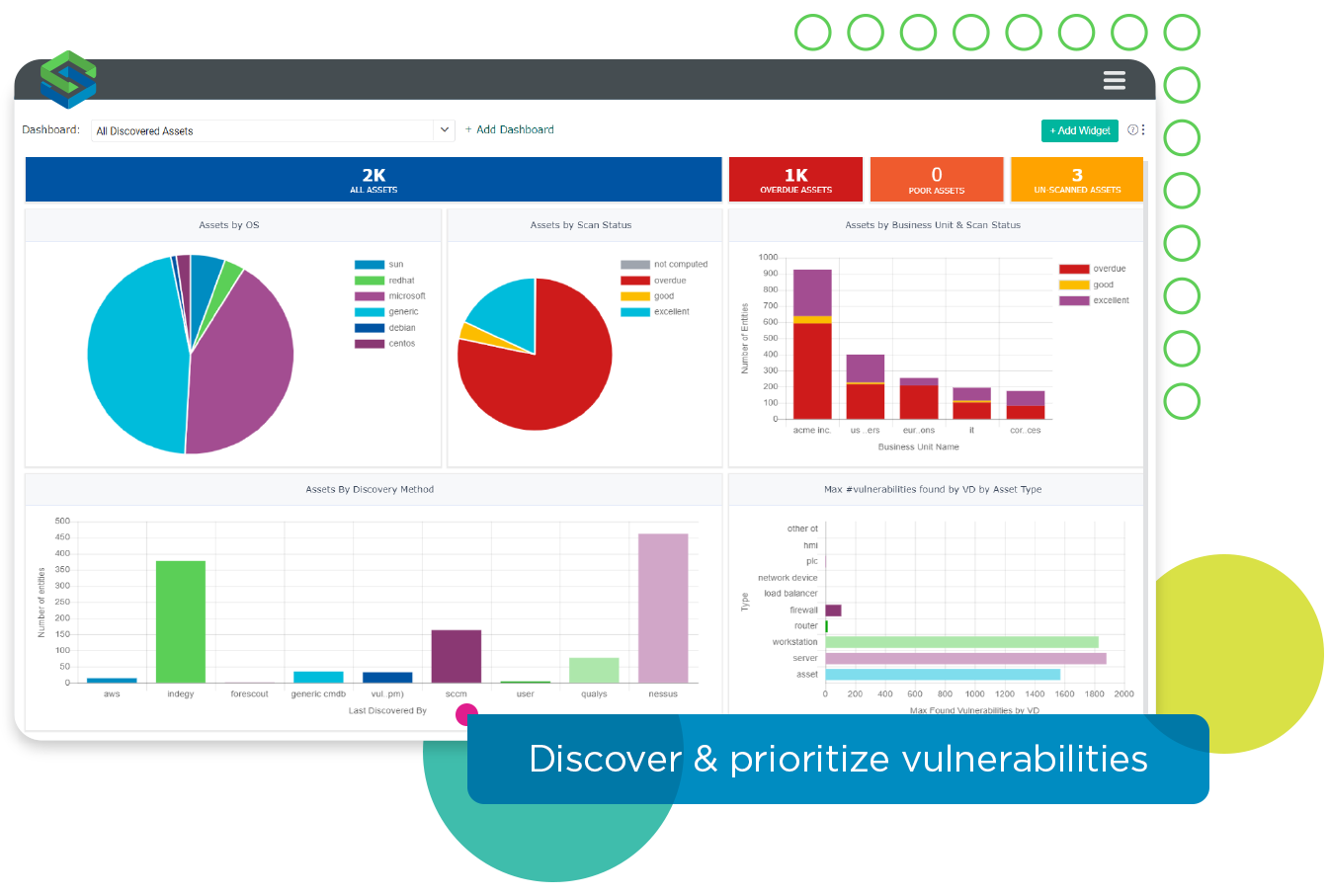
The authoritative reference for vulnerabilities across the organization.
Get the complete picture
Give your team the ultimate vulnerability remediation process to manage threats across your organization. Aggregate scan data from Tenable, Qualys, Rapid7, and others combined with the latest security data, for a consolidated view of the vulnerabilities across the IT estate:
- Combine and de-duplicate scan data for ease of reference.
- Overlay security data from the NVD, published vulnerability repositories, and vendor advisories.
- Consult built-in threat intelligence feeds, and IPS signature feeds from Cisco, Fortinet, HP, McAfee, Palo Alto, and more.
Protect unscannable networks and assets
Ensure difficult or “unscannable” assets and networks don’t get left out of the vulnerability management program. Detect vulnerabilities even in situations where regular scanning would adversely affect performance, or where networks are segregated with air gaps and scanning is not possible:
- Maintain an inventory of the “unscannable” assets in the estate.
- Apply the latest threat intelligence and automatically identify vulnerabilities that are being compromised in the wild.
- Identify compensating controls for situations where immediate patching is not feasible
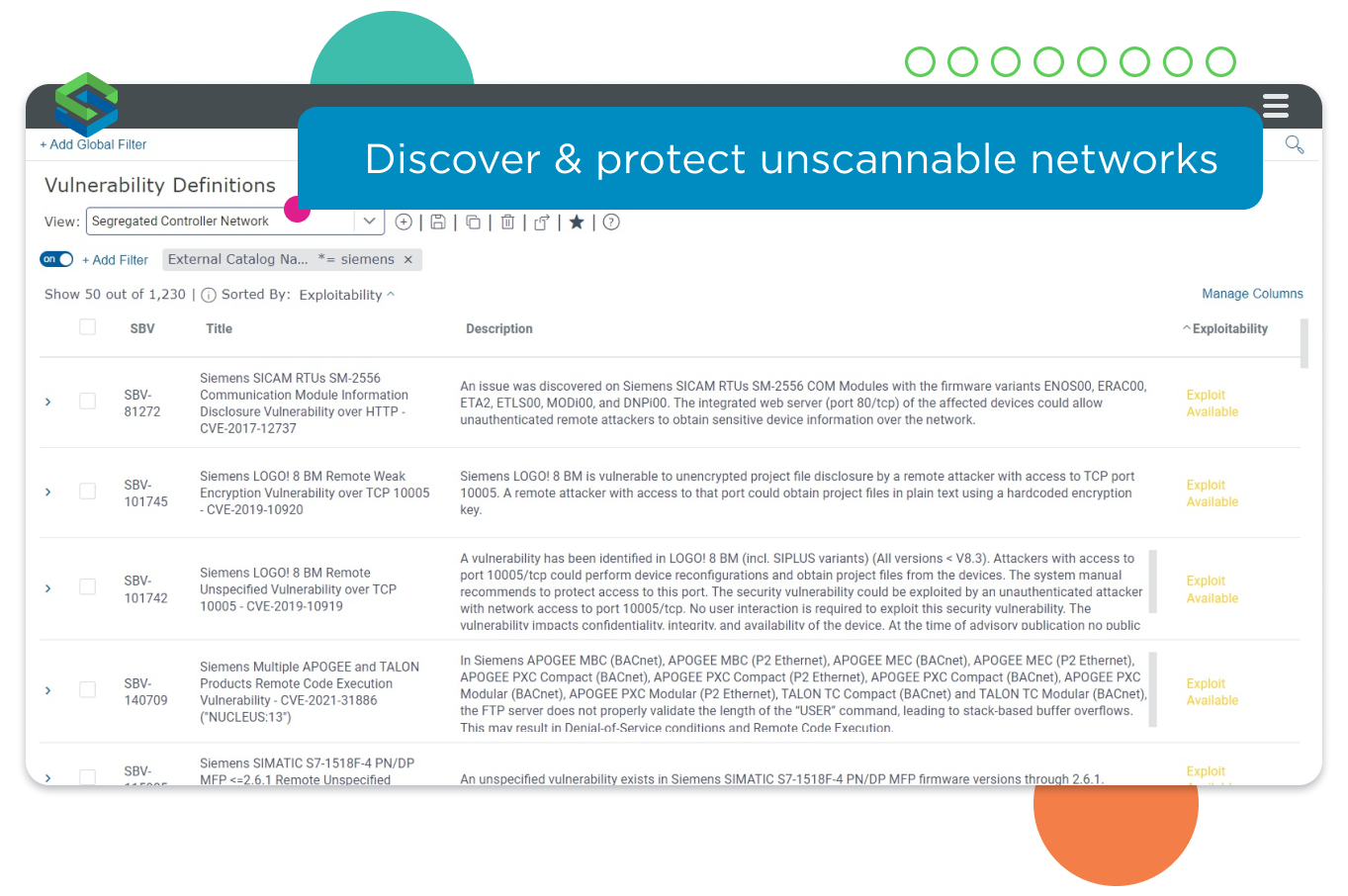
Use scanless detection to identify vulnerabilities on networks that can’t be scanned.
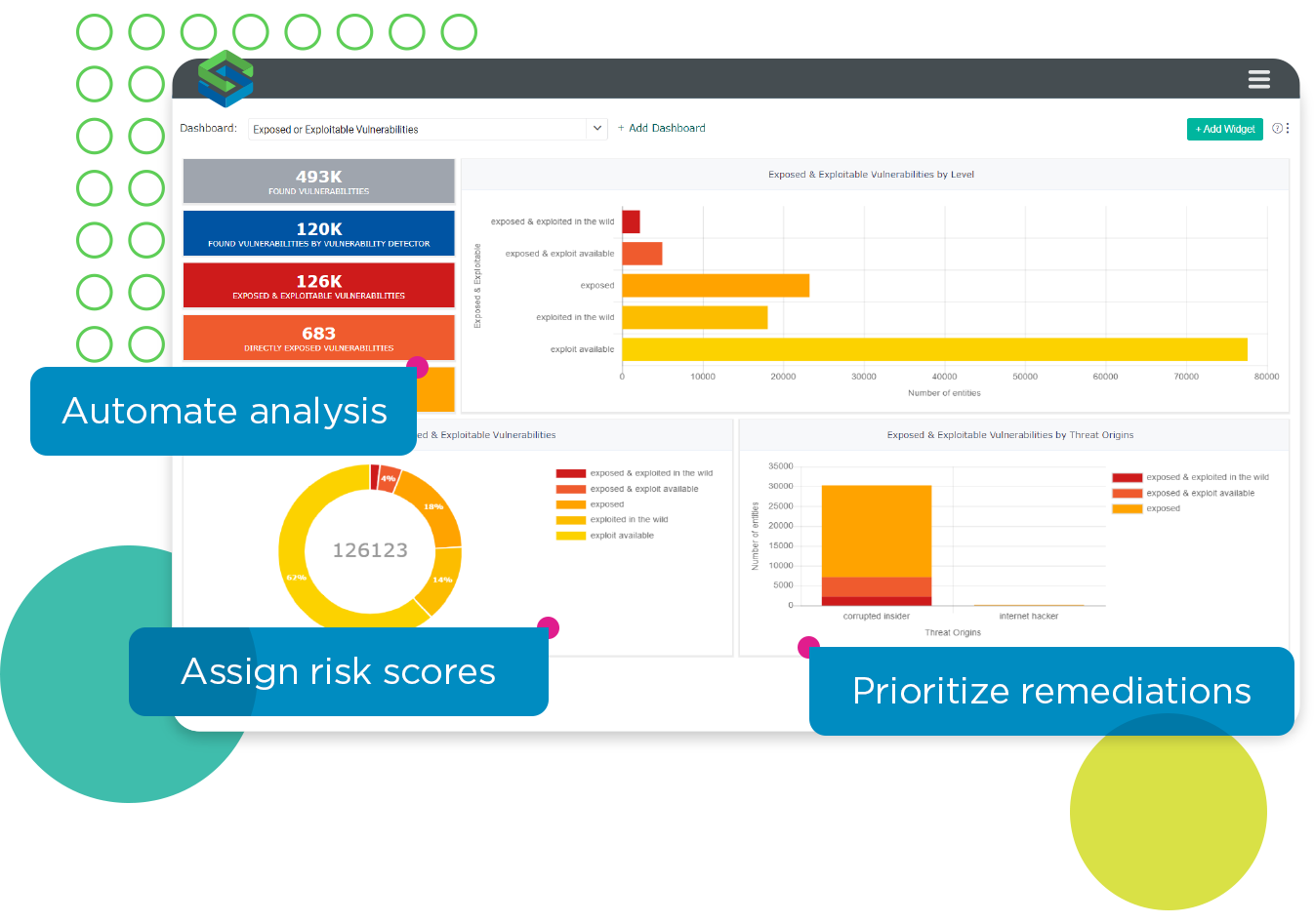
Assess severity, exploitability, business impact, and exposure to prioritize with precision.
Prioritize with precision
Prioritize with precision, reduce critical and high severity vulnerabilities by 80%, and make the scan and patch process 10x more effective. Automatically assess the risk to each asset using Skybox’s unique multi-factor prioritization process and focus the team on what matters most.
Assess the risk in terms of:
- CVSS score
- Evidence of exploitability in the wild, including EPSS predictive scoring for future exploitability.
- Asset importance
- Unique insights into the extent to which the asset is exposed across the network.
Close down attack paths before they close you down
Take prioritization to the next level. See the links and dependencies between potentially vulnerable assets and use attack path analysis to illuminate potential exploit routes. Run exhaustive, non-intrusive attack simulations as part of your red team and penetration testing programs to:
- Simulate attacks on externally facing assets.
- Model lateral movement to identify all the assets an attacker could target.
- Understand the exact route they could take across the network and the compensating controls that would close them down.
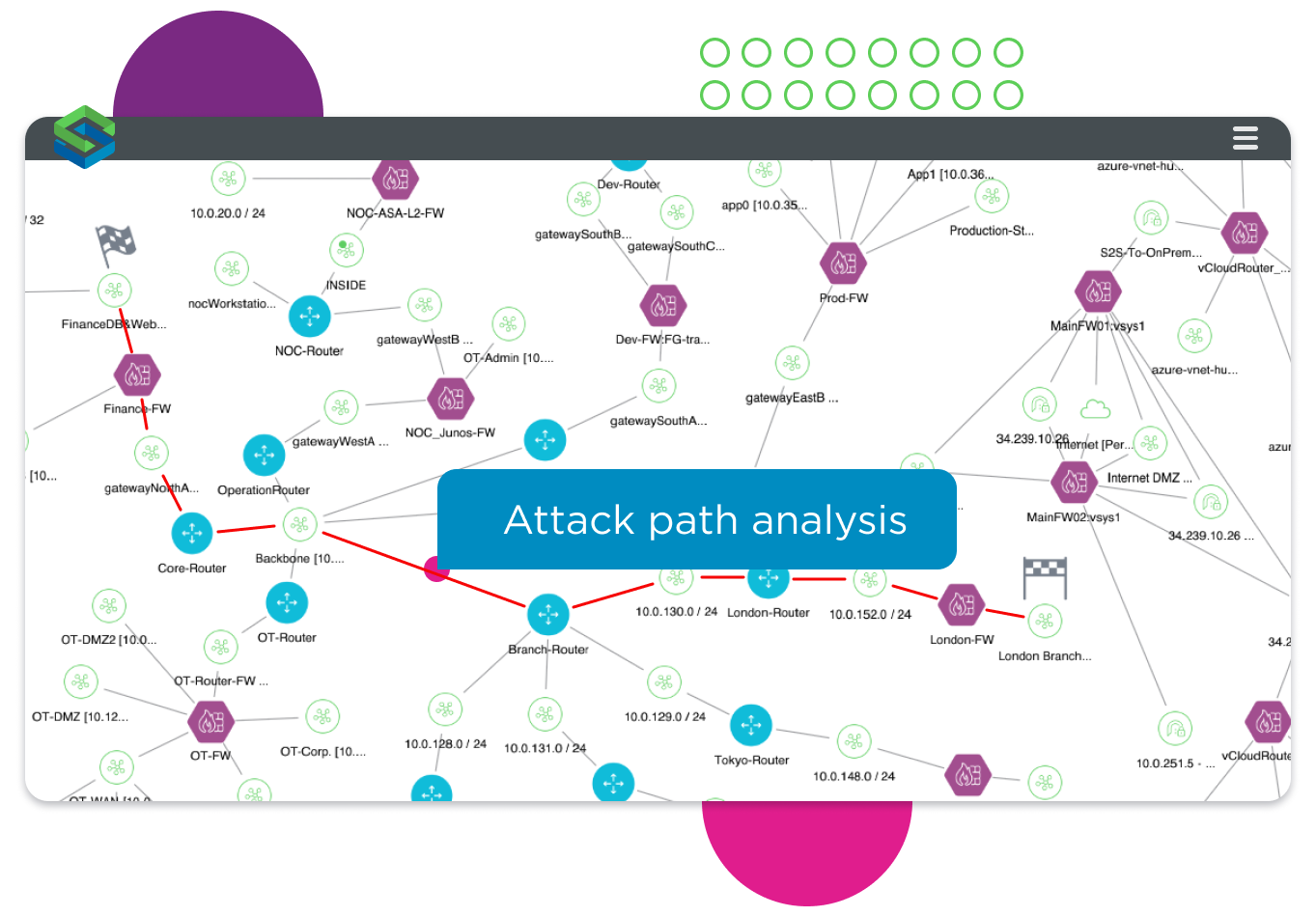
Reveal the exact path(s) an attacker could take across the network to compromise a vulnerable asset.
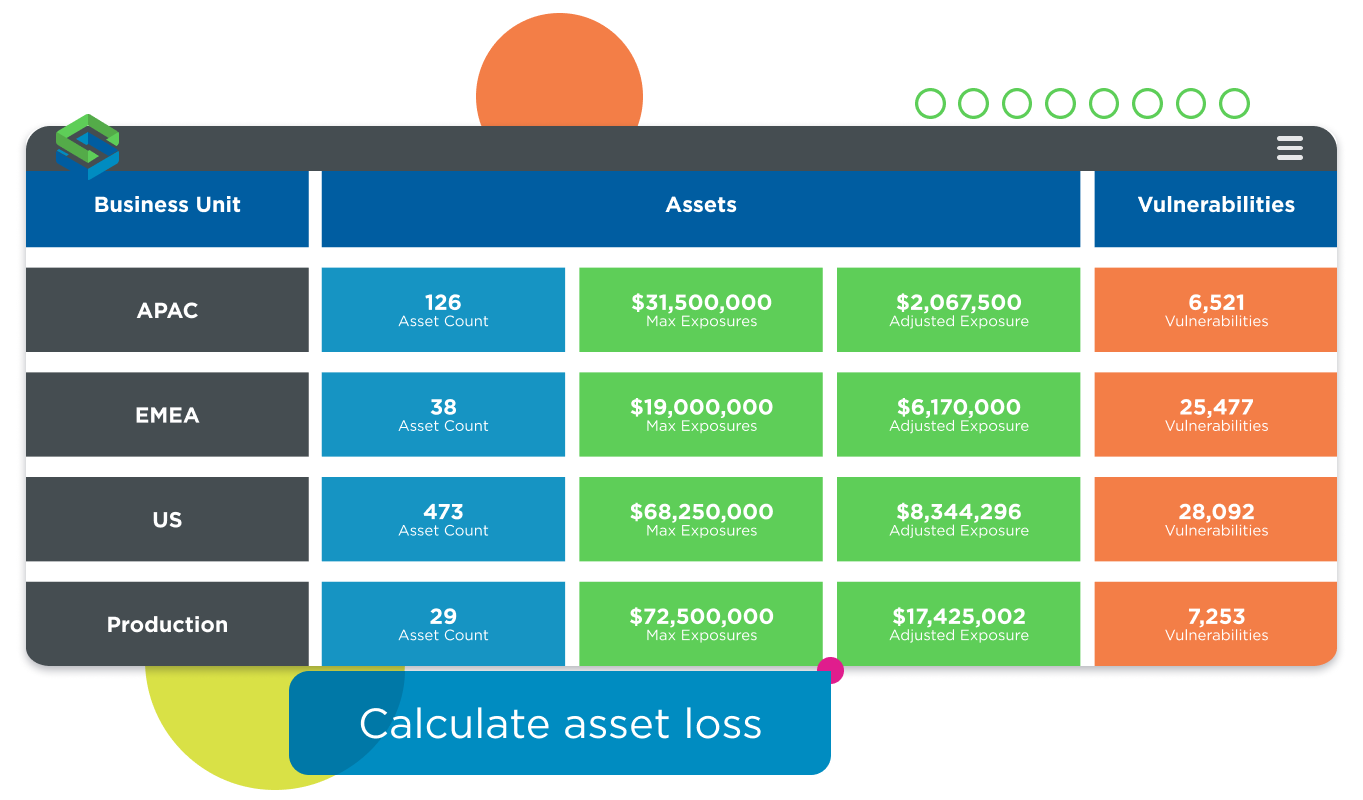
Express cyber risk exposure using the same financial metrics as other business risks.
An unmatched cyber risk quantification tool
Use Cyber Risk Quantification (CRQ) to combine the output from multi-factor prioritization, the number of vulnerabilities hosted on a given asset, and asset value, to report risk exposure in financial terms, and share it with non-technical stakeholders:
- Assess the risk over time and track risk reduction on a per-asset, per-business unit, or organization-wide basis.
- Express cyber risk exposure using the same financial metrics as other business risks.
- Leverage CRQ to help Increase awareness, secure resources, and focus the organization on protecting critical assets.
Slash remediation times from weeks to hours
Scan and patch cycles often take weeks to address even the most critical and high-severity vulnerabilities, leaving countless vulnerabilities on key assets exposed to potential compromise for lengthy periods. Slash the Meant Time to Remediate (MTTR) and close the scan and patch gap from weeks to hours.
- Accelerate MTTR by scanning the Skybox security model, rather than the IT estate.
- Automatically analyze the risk based on an in-depth knowledge of network exposure.
- Select from a choice of prescriptive remediations, including patches and software upgrades, IPS signature updates, and firewall rule changes.
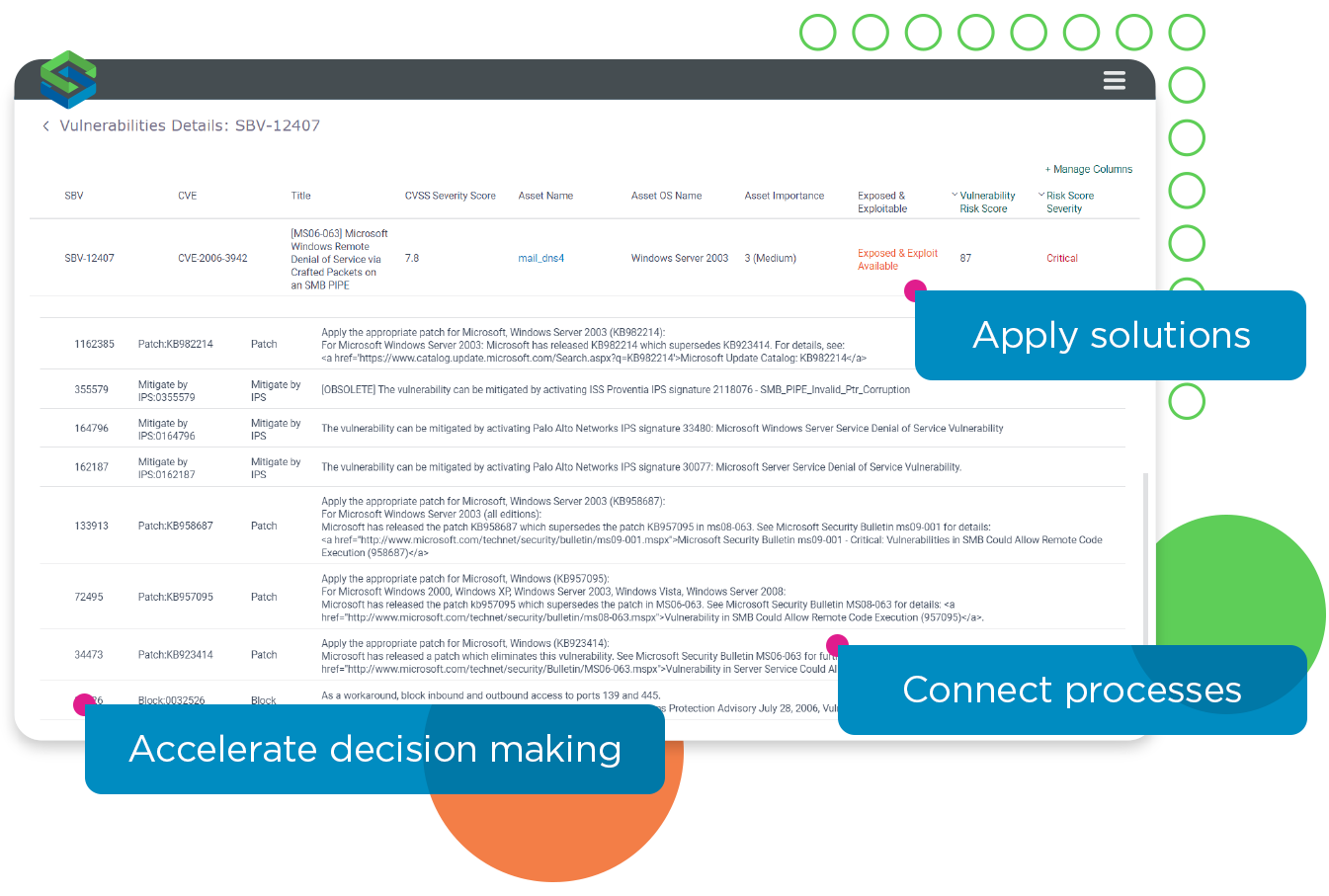
Skybox automatically provides a range of possible compensating controls for situations where immediate patching isn’t possible.
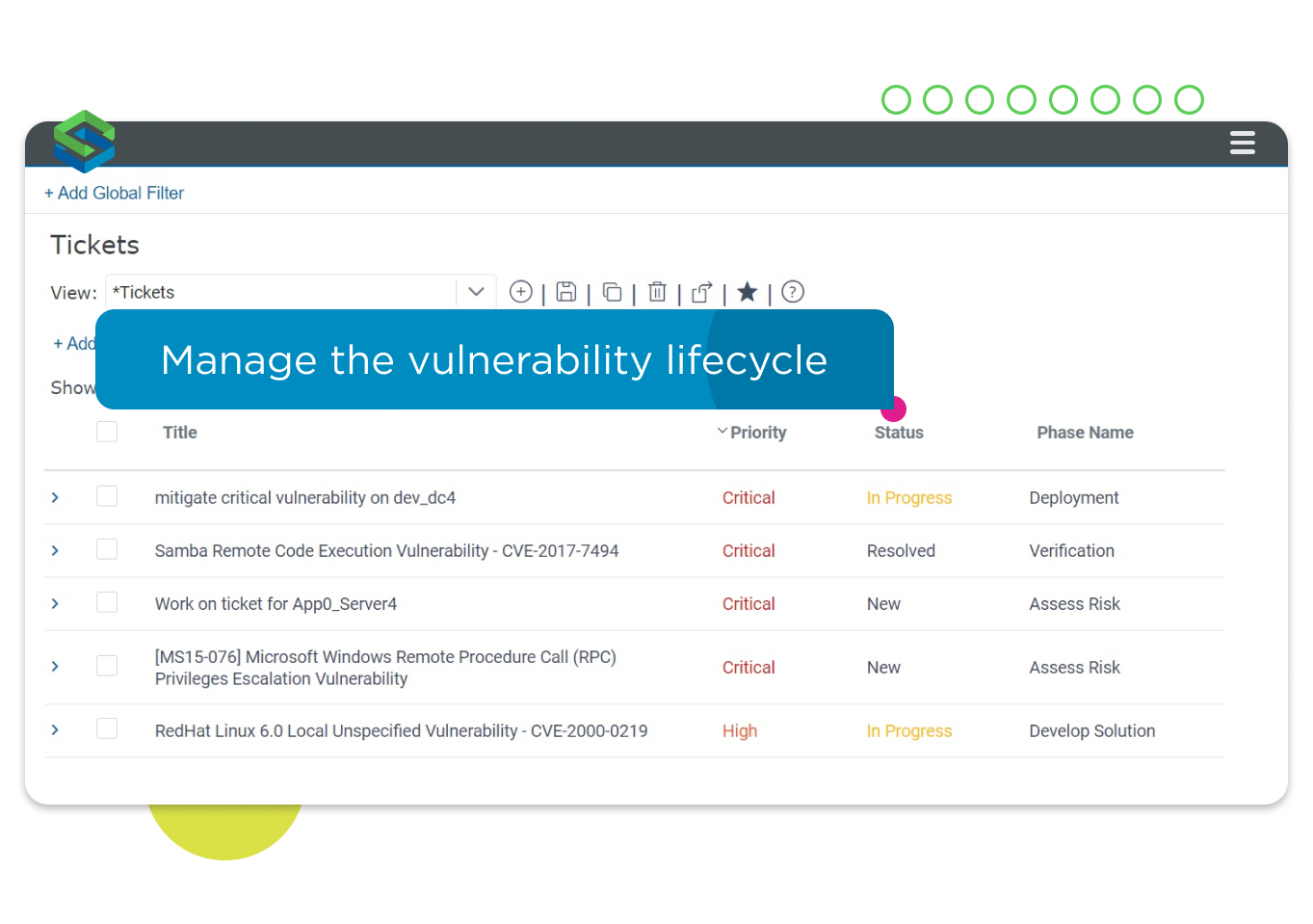
Orchestrate and validate the entire remediation process.
Automate the response
Automate the vulnerability remediation process using a built-in ticketing system, or by integrating Vulnerability Control seamlessly with your chosen SOAR/ITSM solution to orchestrate and validate the remediation process. Track the effectiveness of your vulnerability management program over time:
- Report on open and overdue tickets, patching efforts, and overall progress against SLAs.
- Generate executive and compliance reports for internal/external auditors.
- Quantify the risks, translate them into financial metrics, and report them to senior stakeholders.

The authoritative reference for vulnerabilities across the organization.

Orchestrate and validate the entire remediation process.