Model Explorer
Enjoy total visibility and maintain constant vigilance across the ever-expanding attack surface, with Model Explorer.
Attack Surface Management:
Inventory your assets, identify and eliminate cyber security risks, and secure your networks, with the Skybox Attack Surface Management solution:
- Continuously monitor every attackable asset and application.
- See where cybercriminals could penetrate and move through your network.
- Identify security exposures, potential attack paths, and their resulting blast radius.

The authoritative reference for attackable assets across the organization.
Inventory every asset
Stay ahead of attack surface challenges with a comprehensive inventory of every attackable asset in the organization. Model Explorer automatically discovers and continuously maintains a repository of all the attackable assets in the Skybox Dynamic Security Model, including:
- Physical and virtual computing assets, cloud workloads, and containers.
- Applications, services, operating systems, and patches.
- Network infrastructure, routes, rules, access, and security policies.
See the business context
Cyber exposure is about more than just technology, so Model Explorer overlays the business context you need to understand and reduce your attack surface. Connect to organizational directories, extract, and incorporate business information including:
- Geography and organizational business unit data.
- Applications, the assets they are hosted on, and the services they are running.
- User information, including permissions, login dates, and even password expiration.
- Cyber risk quantification values and risks.
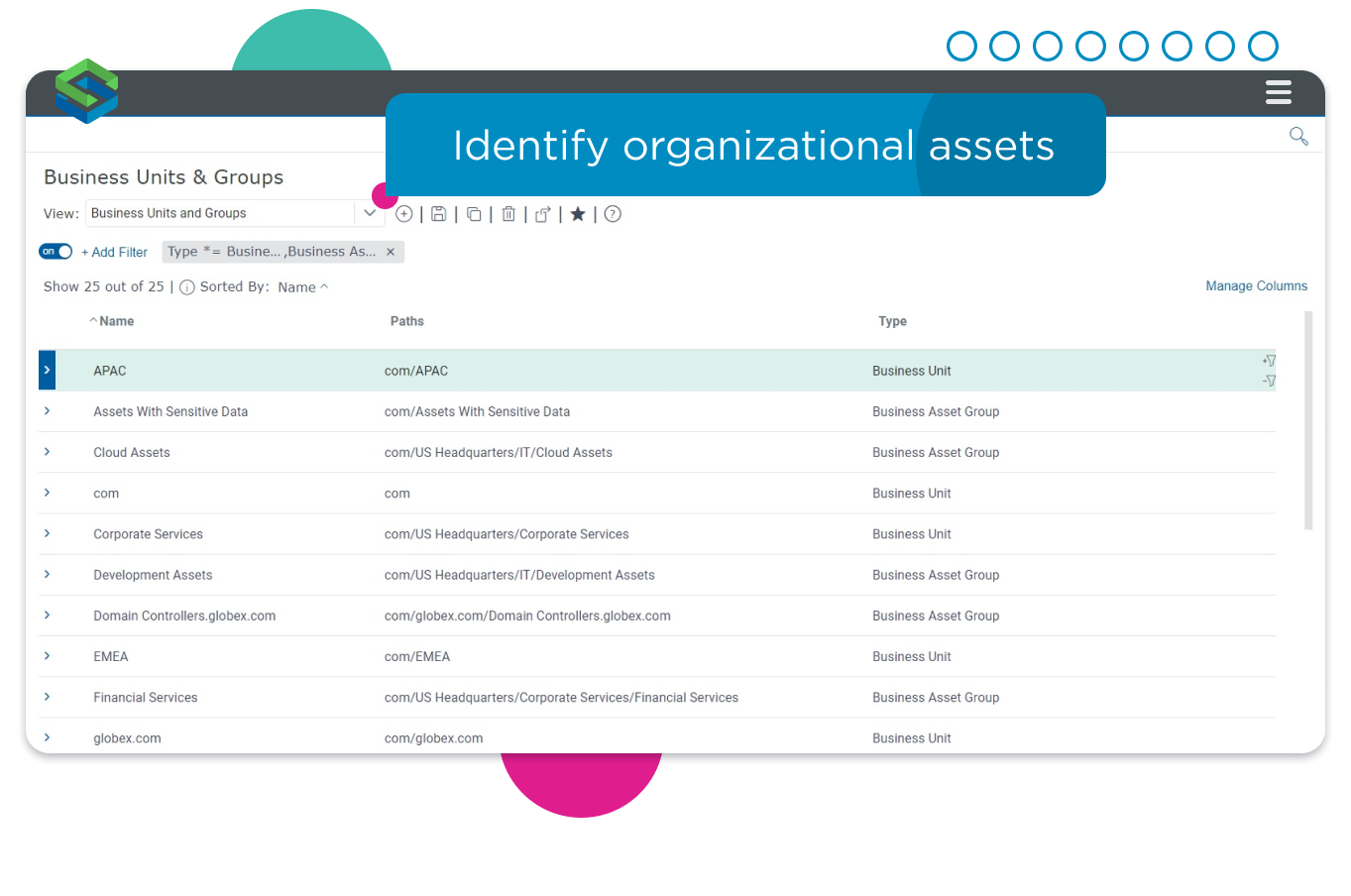
Include business units, locations and users in the asset inventory.
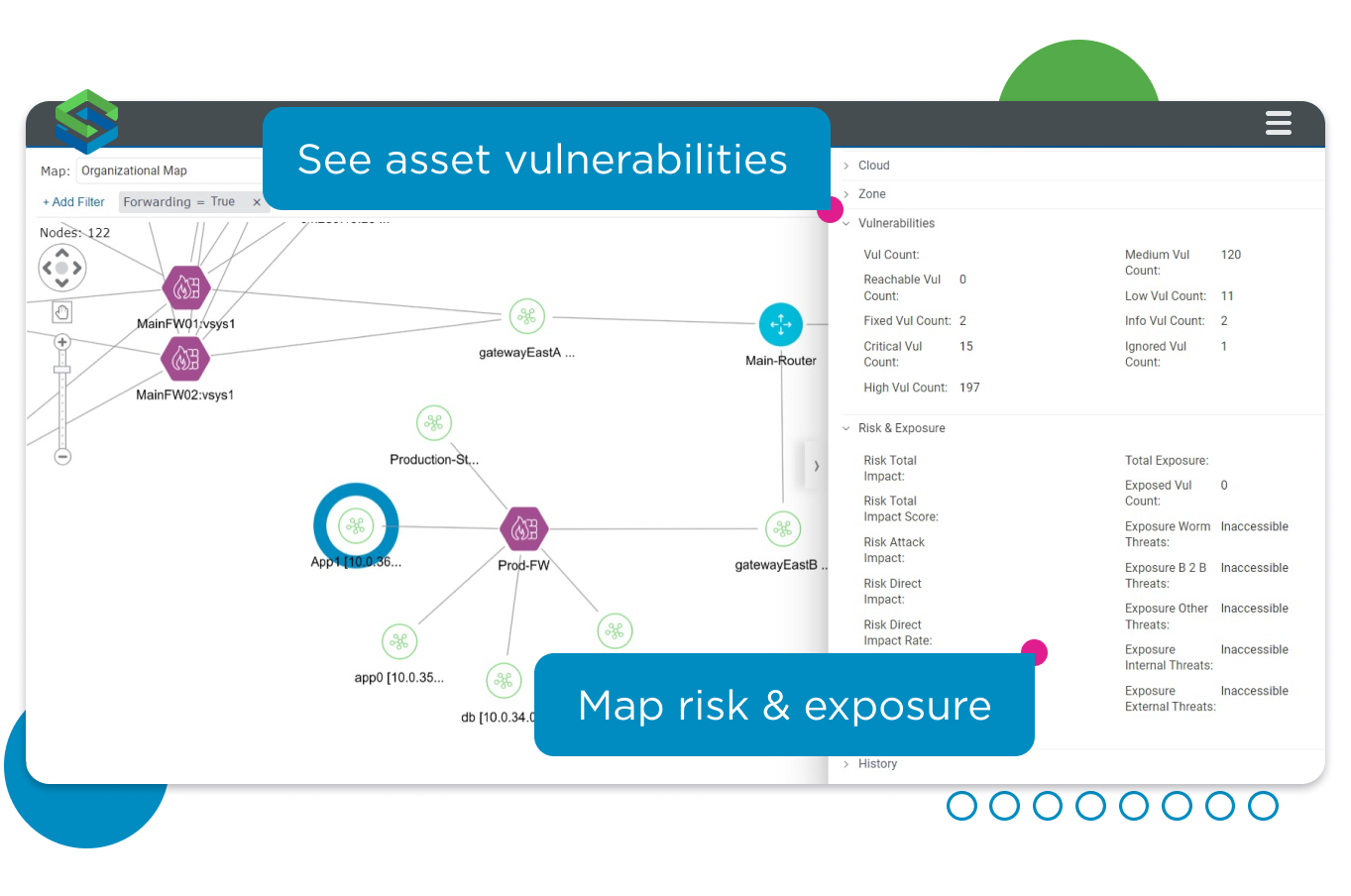
Get the essential network context needed to understand exposure.
Build actionable attack surface mapping
Use Model Explorer to navigate the Dynamic Security Model and get the essential attack surface analysis you need to understand your exposure. From a bird’s eye view to a detailed drill-down, explore every aspect of the attack surface, including:
Assess the risk in terms of:
- Network topology, and segmentation.
- The relationship between assets, networks, and the devices that connect them.
- Asset vulnerabilities, risk, and exposure metrics.
Zero in on high-risk assets
Continuously monitor high-risk assets, such as those that are externally facing, to better understand organizational exposure. Identify those high-risk assets that host vulnerabilities that are, or likely will be exploited by threat actors:
- Use exposure analysis to query the Skybox model, rather impacting physical networks and devices.
- Identify vulnerable applications and the assets and services they are hosted on.
- Make smarter risk assessments that factor in CVSS score, current and likely exploitability, asset importance, and network exposure.
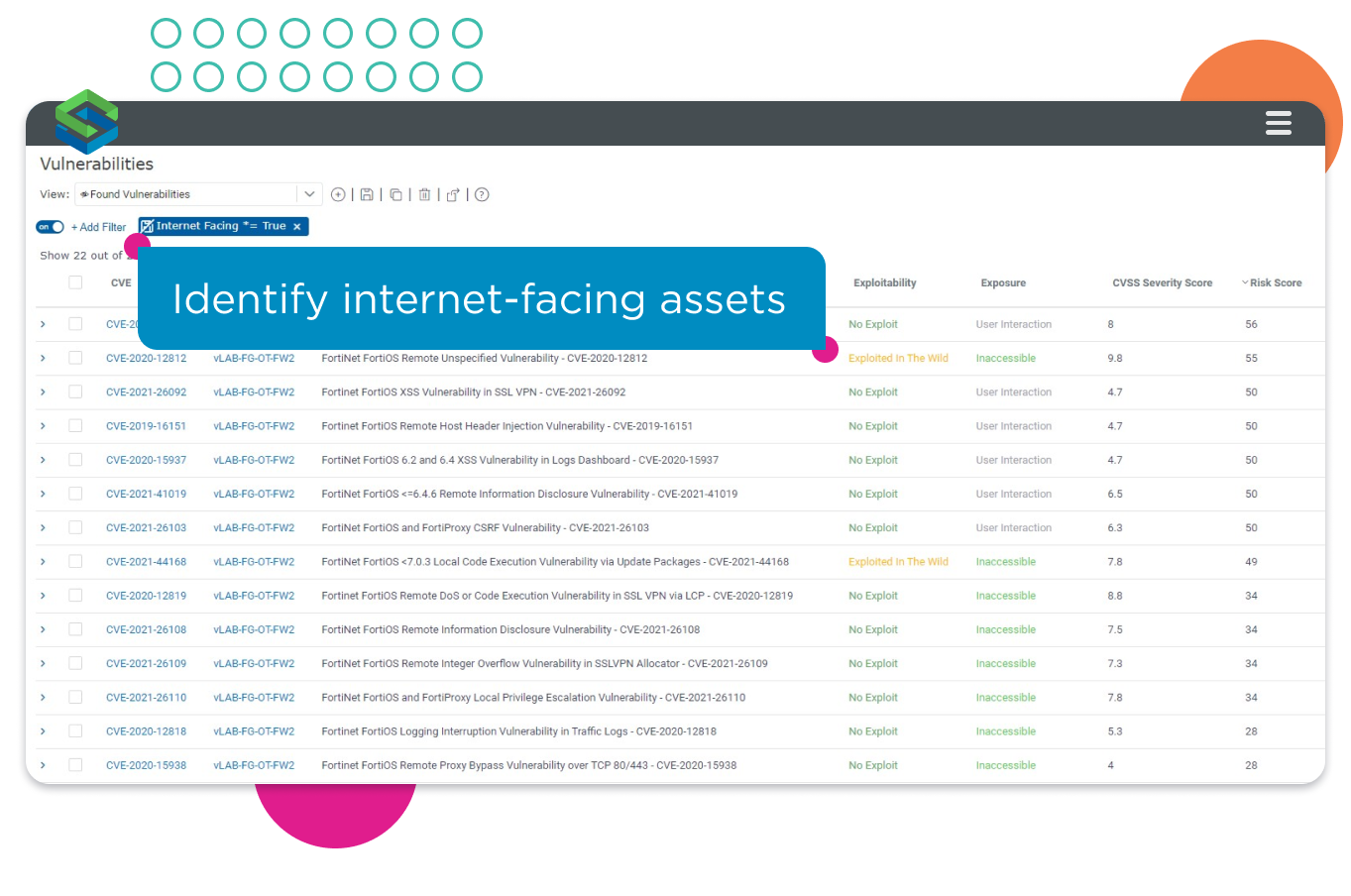
Identify vulnerable high-risk and internet-facing assets.
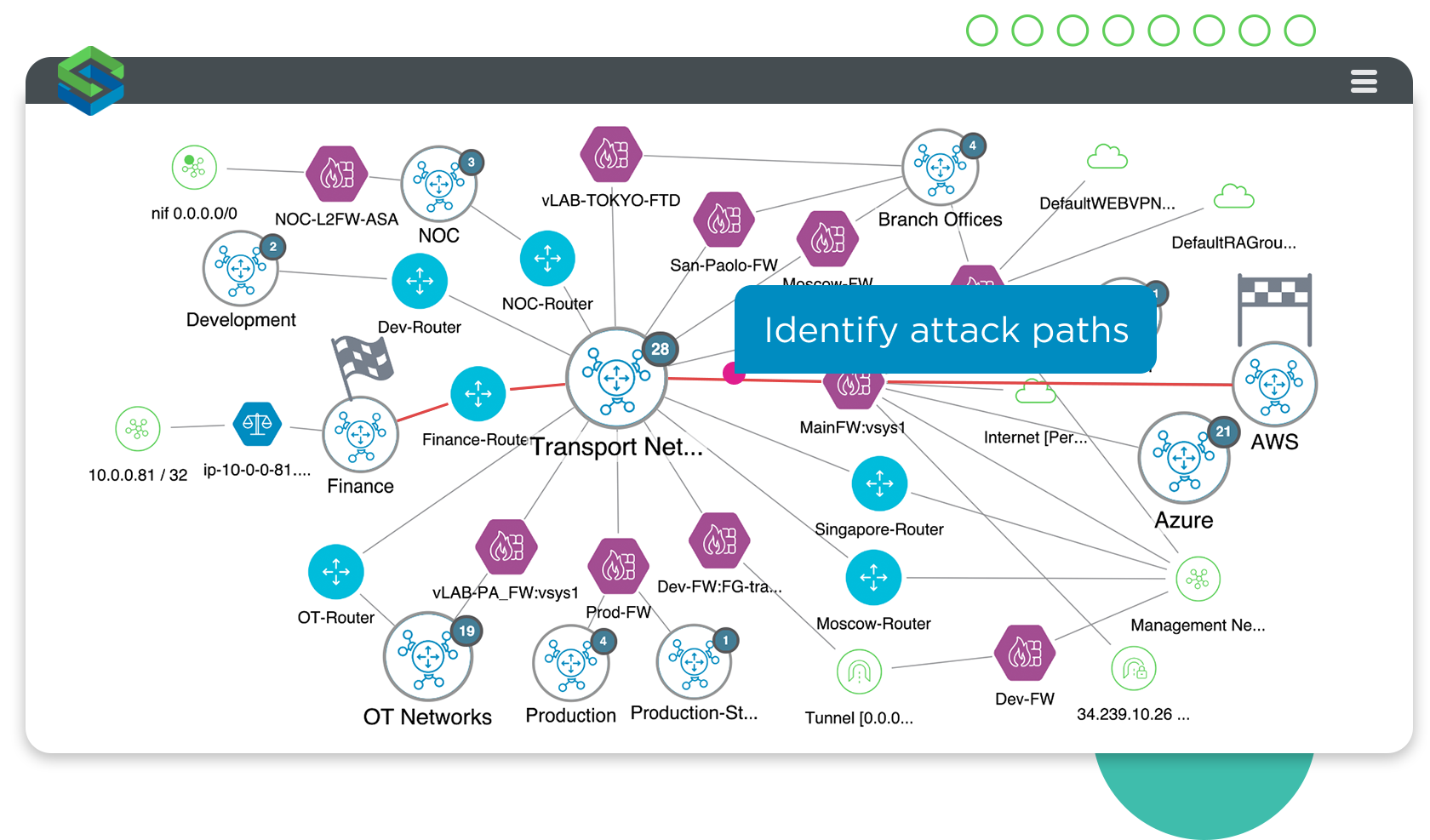
Model the exact route(s) an attacker could use to compromise assets.
Pinpoint attack paths
See your attack surface like an attacker would. Identify the attack paths a threat actor could take to access key assets in the organization. Run exhaustive, non-intrusive attack simulations as part of your red team and penetration testing programs to:
- Zoom in on potential entry points for attackers.
- Analyze connections to supply chain and partner networks.
- Model lateral movement and understand the exact route an attacker could take across the network.
Simplify cyber asset management
Create custom views of the Dynamic Security Model to suit organizational needs by adding network and asset groups and hierarchies as well as information about specific business units and locations. Generate cyber asset inventory reports that:
- Simplify asset management.
- Reduce manual processes.
- Support compliance and audit initiatives.
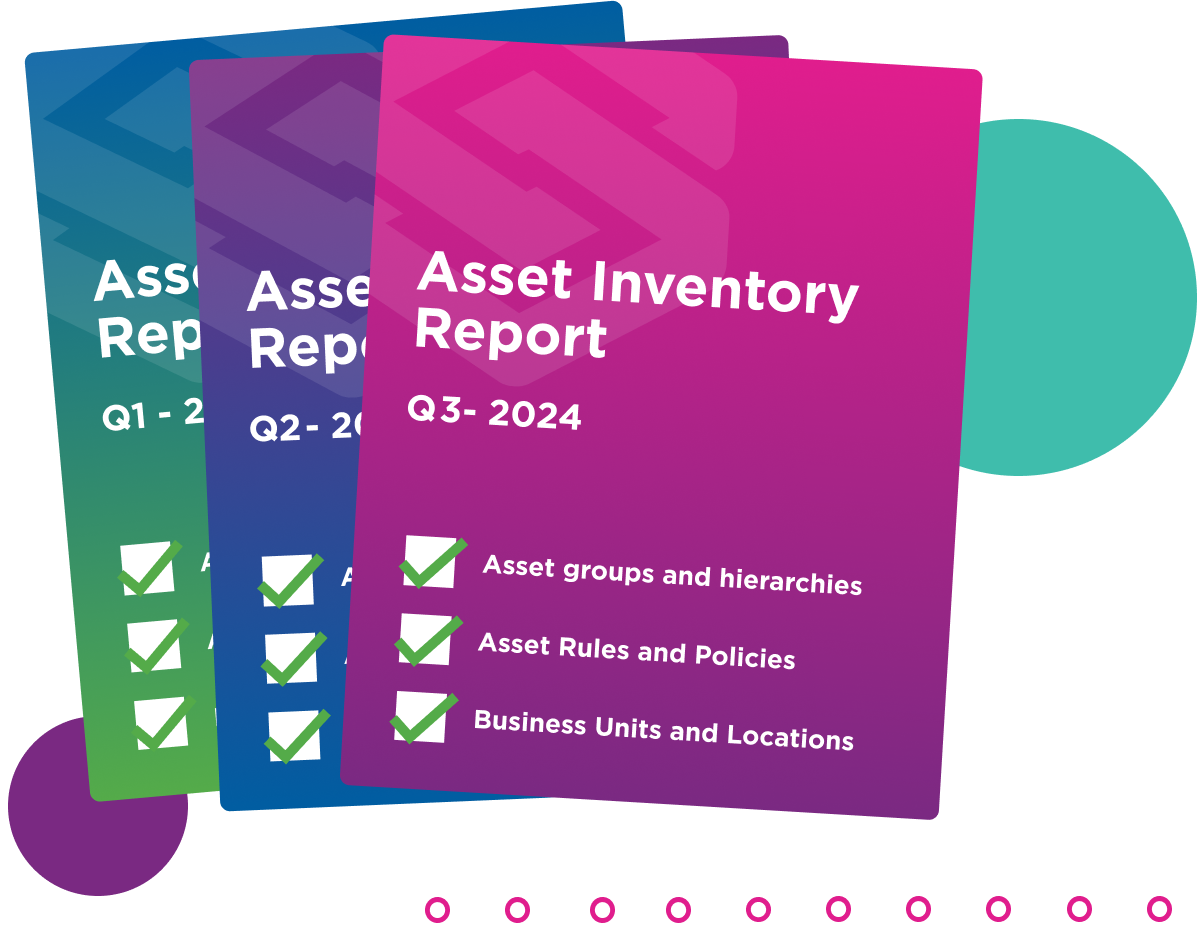
Automatically generate asset inventory reports for ease of management.
Related Skybox Products
These Skybox Products include Model Explorer, enabling you to discover and inventory attackable assets and visualize the attack surface.

The authoritative reference for attackable assets across the organization.

Identify vulnerable high-risk and internet-facing assets.

Model the exact route(s) an attacker could use to compromise assets.