Skybox Cloud Edition
The first complete SaaS solution for managing security policy in hybrid multi-vendor environments. The most flexible deployment options for vulnerability risk prioritization.
See how Skybox Cloud Edition helps you gain visibility and control over your network security to combat threats.
Stay continuously compliant. Prevent breaches before they happen. Get the intelligence and context you need to reduce cyber exposure with Skybox Cloud Edition.
Managed in the cloud, Skybox Cloud Edition is our existing award-winning Continuous Exposure Management Platform, now available as a service.
Hosted in multi-tenant AWS for outstanding reliability and availability, Network Assurance Cloud Edition, Firewall Assurance Cloud Edition, and Vulnerability Control Cloud Edition modules are currently available. Whatever the use-case, from network compliance analysis and firewall rule optimization to vulnerability discovery, prioritization, and remediation, our Cloud Edition modules strengthen your security posture.
Learn how Cloud Edition can help with your use-case:
You are moving applications to the cloud. Skybox Cloud Edition protects your assets.
During your multi-year cloud transition journey, you need a modern, complete SaaS solution to visualize the attack surface, manage security policies, and protect your vulnerable assets in a complex multi-vendor environment of on-premises and multi-cloud technology stacks. Skybox Cloud Edition seamlessly aligns with your cloud transition journey and technology adoption roadmaps to de-risk the application migration process.
Security fatigue is real. Skybox Cloud Edition reduces your operational burden.
We know your technical resources are precious, and there aren’t enough hours in the day for all the alerts and urgent tasks that come your way. Skybox Cloud Edition reduces your operational burden significantly, leaving you free to focus valuable personnel where they are most needed. Rapid onboarding decreases time-to-value by offloading to Skybox many administrative tasks such as software upgrades, server software installation, server hardware, VM and OS maintenance, service health monitoring, and backups/DR.
You cannot afford unplanned downtime. Skybox Cloud Edition guarantees solution availability.
The service includes a 24×7 NOC and SOC. Continuous monitoring by Skybox experts assures you of optimum solution performance, eliminating bottlenecks and maintaining a robust network and cloud security posture. Guaranteed service level agreements ensure solution availability and reliability.
You need instant access to Skybox innovations. Skybox Cloud Edition includes seamless upgrades.
Cloud Edition product modules are always updated with the latest capabilities, as Skybox orchestrates seamless software upgrades when new releases become available.
Skybox Cloud Edition comprises these award-winning product modules
Vulnerability Control Cloud Edition – for vulnerability discovery, prioritization, and remediation.
Firewall Assurance Cloud Edition – for optimized firewall policy management and robust cyber hygiene.
Network Assurance Cloud Edition– for continuous network visibility, analytics, and compliance.
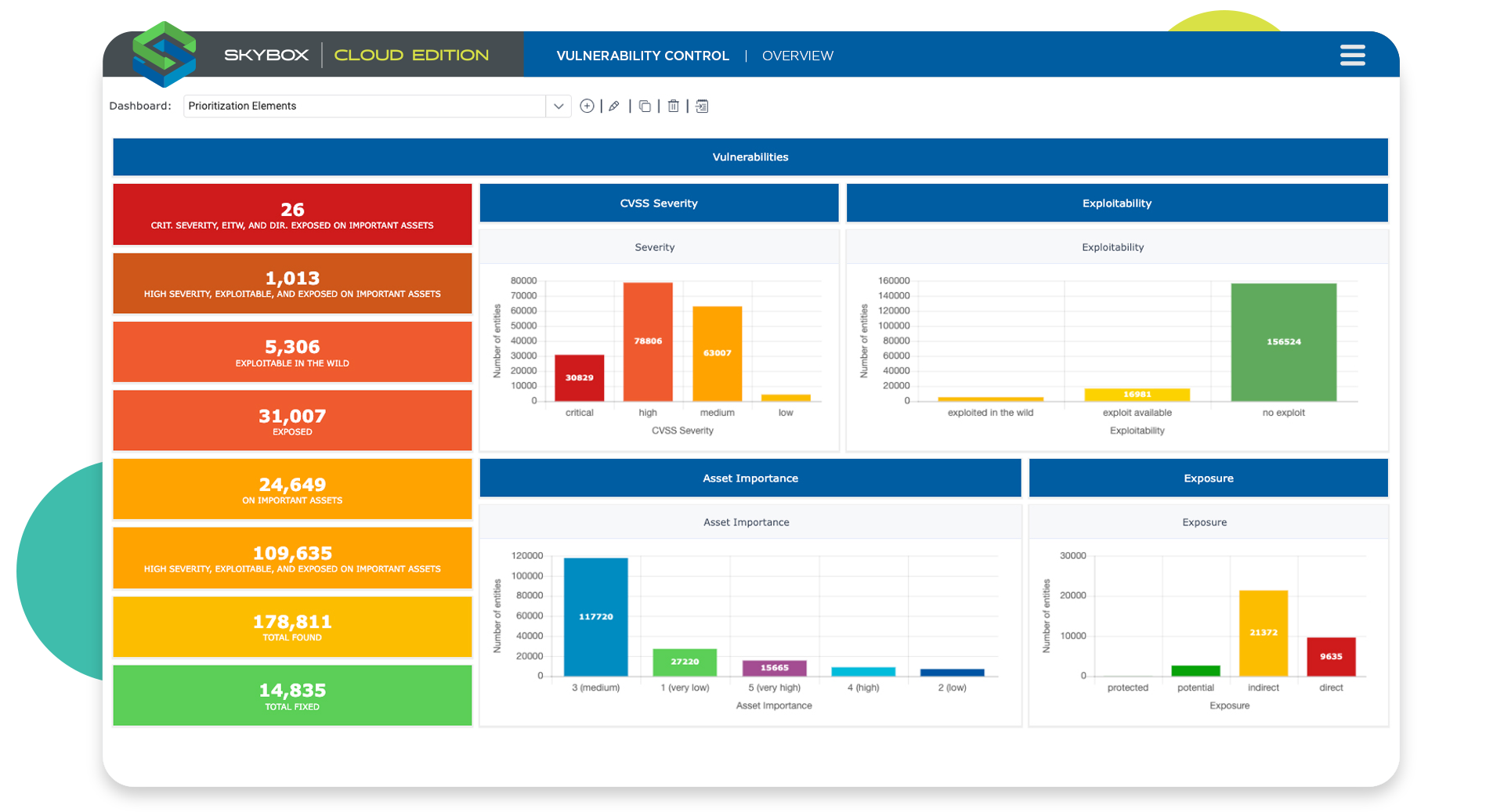
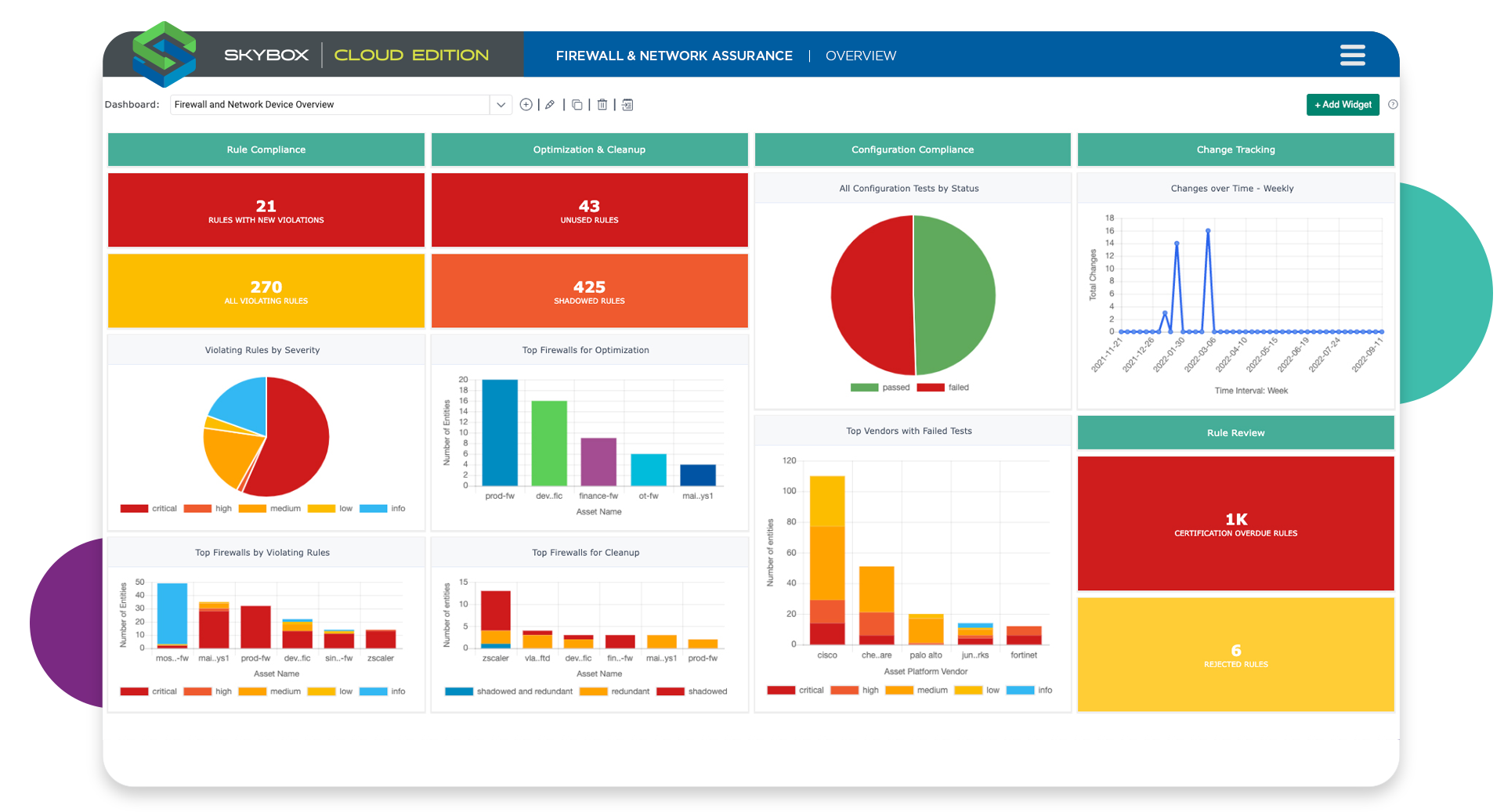
Teams need a complete picture of their network topology to protect investments, simplify audit and compliance, and maximize...
With automated rule lifecycle management, compliance audits are faster, rule changes are more precise, and cyber security risk assessments...
Prioritize remediation of vulnerabilities with intelligent analysis of cyber exposure across the threat landscape.
