External Attack Surface Management (EASM)
The Skybox Continuous Exposure Management Platform provides a consolidated model of your security environment that is updated automatically and continuously, enabling you to conduct a detailed analysis of your exposure to attack on the model instead of on the live networks and devices.
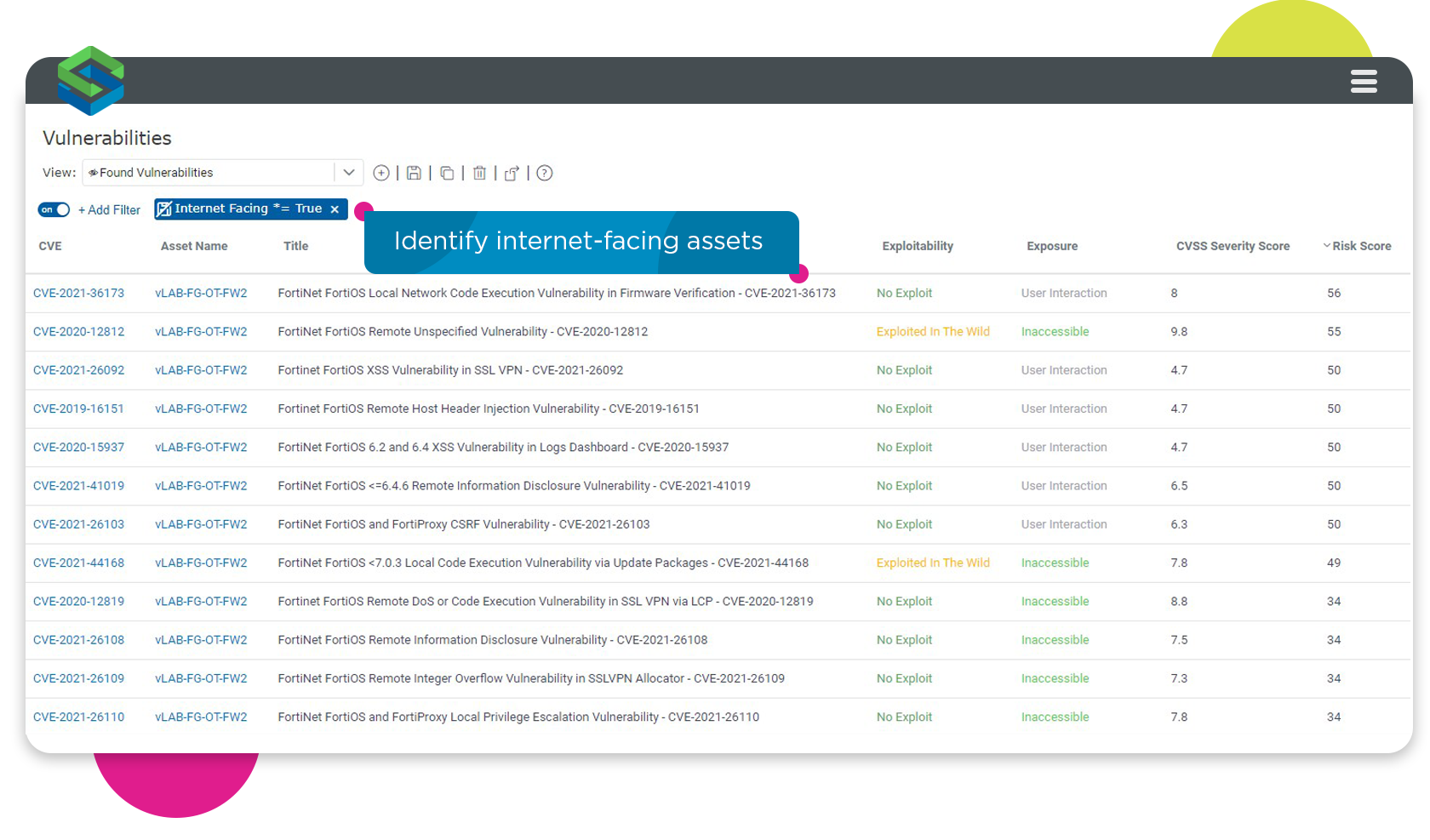
Version 13.1 now incorporates new External Attack Surface Management (EASM) capabilities to help customers see their organizational attack surface from an attacker’s point of view.
Skybox automatically runs an analysis against the network model to detect all the internet-facing digital assets and networks in the organization and to find all the existing vulnerabilities in your organization that belong to those internet-facing devices.
Enhanced attack simulation and visualization capabilities
With Version 13.1, Skybox has enhanced and simplified the attack visualization process, enabling the security team to quickly see how an attacker could exploit a vulnerability and how best to mitigate the threat. This essential capability is only possible because of the unique way that Skybox models the attack surface, combining networking data, vulnerability data, and security policy to visualize every aspect of an attack.
This unique visualization capability complements traditional assessment methods, enhancing the effectiveness of vulnerability management and penetration testing initiatives.
Customers can now conduct exhaustive, nonintrusive attack simulations against the model to measure the effectiveness of potential threats in penetrating security defenses. Skybox determines which assets are reachable and exploitable, and which assets are secure.
This analysis enables IT departments to identify the exposed vulnerability occurrences that make up the primary risks to critical assets. Working from this analysis, security and IT professionals can focus on critical exposures when they occur and reduce the time to remediation from weeks to hours.
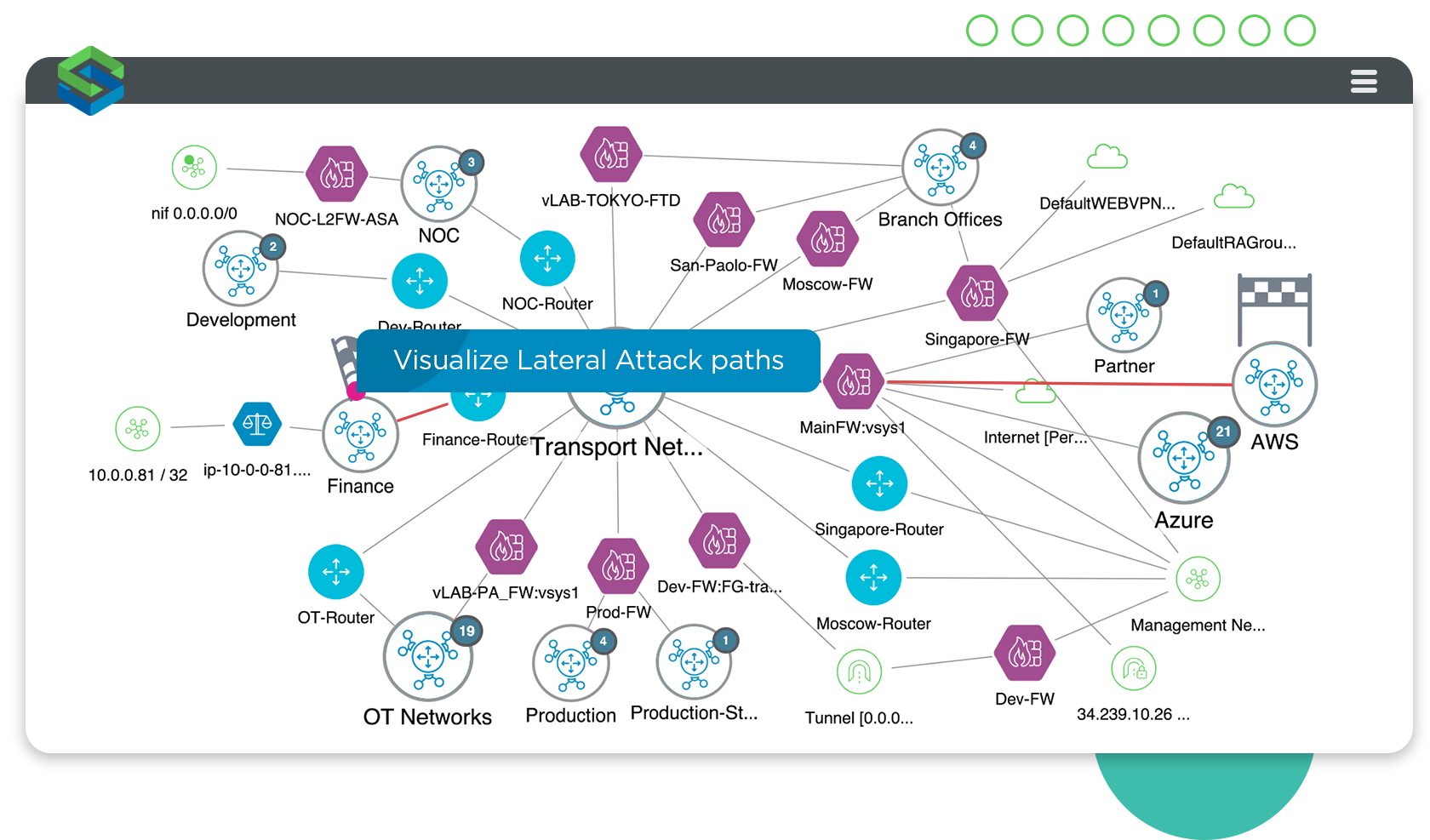
Lateral movement visualization
Customers can now simulate lateral movement attacks using the Skybox model’s unique understanding of the underlying networking and security policy data to identify all the potential targets that could be attacked if an asset hosting a given vulnerability was exploited.
Skybox visually models the result, providing a “blast-radius” assessment that shows all the assets an attacker can access from the source asset.
As new threats emerge, or as an attack develops, the security team can use this analysis to rapidly identify compensating network controls such as IPS signature updates or access rule changes that could be used to mitigate the threat.
Additional enhancements
Version 13.1 also includes key enhancements to the Skybox Security Policy Management solution.
Customers can now incorporate URLs and URL categories configured in Palo Alto and Checkpoint firewalls into their firewall rule reviews, rule compliance checks, and access rule recertification workflows.
Building on the application provisioning support introduced in Version 13.0, customers can now provision new access rules and modify existing access for application-centric rules in Palo Alto firewalls.
Learn more about 13.1
Find technical documentation for the Skybox version 13.0 release in the Documentation Portal. As always, technical support is available via the Customer Support Portal.