With enterprises focusing on increasing security maturity and setting out their plans to achieve a Zero Trust security posture, we will see SASE continue to gain potential and drive the demand for a proactive and holistic security posture management program.
SASE is the unification of security and networking solutions together under a single unified cloud-based platform, enabling collaboration between two historically disparate operational silos. SASE enables efficient and effective access control and edge protection. By gaining context and visibility and applying automation, organizations can improve security posture and risk management.
What is SASE?
According to Gartner®, “IT architectures are evolving in the face of demands for scalability, flexibility and increased security, and because of network challenges, such as low-latency and WAN edge requirements. This broad set of drivers defines a unified service model for cloud-delivered networking and security called secure access service edge (SASE). Cloud security architects must be cognizant of these developments, and, as cloud and distributed services grow, must implement SASE-aligned capabilities.”1
SASE adoption increases
Accelerated by the pandemic, protecting the edge tops the priority list for many organizations. A surge of home offices came online that needed protection and security, just like a data center. This shift to a work-from-anywhere model put significant strain on IT organizations and continues to do so. Many of these employees will continue to work from home, despite lifting Covid restrictions. IT and security organizations are being asked to extend security coverage in a flexible and manageable way that will be resilient if faced with future disruptions. As a result, we will see a steady increase of security solutions, such as SASE and SDWAN, throughout this year and beyond.
According to Gartner, “By 2025, at least 60% of enterprises will have explicit strategies and timelines for SASE adoption encompassing user, branch, and edge access, up from 10% in 2020.”
2
Where SASE and Zero Trust intersect
SASE leans heavily on a Zero Trust security model, which does not grant a user access to applications and data until their identity has been verified — even if they are already inside the perimeter of a private network. When establishing access policies, a SASE approach takes more than an entity’s identity into account; it also considers factors like user location, time of day, enterprise security standards, compliance policies, and an ongoing evaluation of risk/trust.
However, many organizations struggle to implement Zero Trust frameworks due to environment complexity and lack of attack surface visibility. Massive, fragmented networks, decentralized, inconsistent configurations and change management processes, unsafe cloud and network configurations, and the continual increase in vulnerabilities have created the perfect storm. Companies invest millions in security controls to block, detect, prevent, or respond to attacks; despite this, we see vulnerabilities and misconfigurations across their hybrid environments routinely exploited.
Full network visibility and context needed to reap SASE benefits
This is where Skybox comes in. To make Zero Trust a reality and maximize the full benefits that solutions like SASE can provide, organizations need complete visibility and context across their entire hybrid, multi-cloud, and OT network environments. The Skybox Security Posture Platform provides just that.
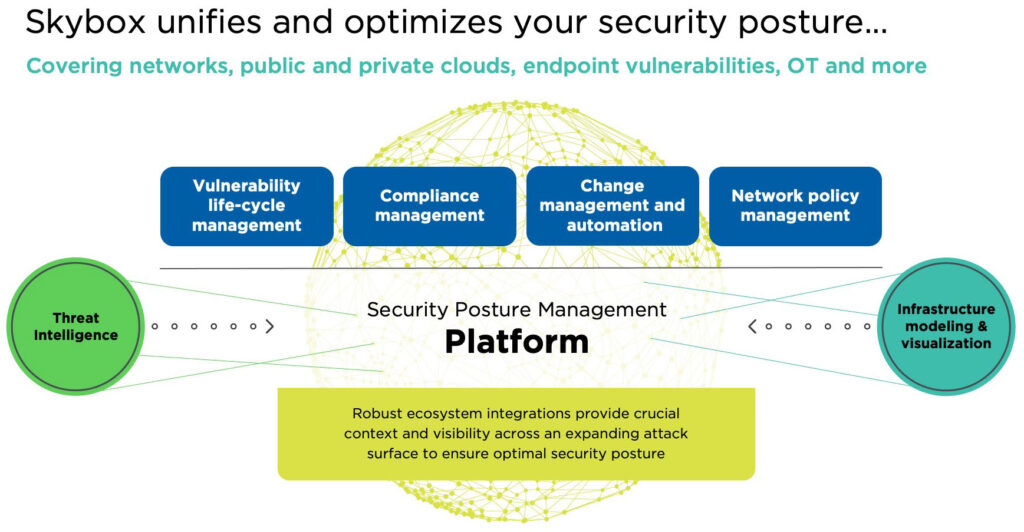
Our customers use the Skybox Security Posture Management Platform to aggregate and centralize complete sets of data that reflect their security controls and network configurations across all domains – from on-premise data centers, public and private cloud networks, OT networks, and across all networks that connect their various business locations, users, assets, and applications. With these rich data sets, the Skybox platform can model the customer’s hybrid network allowing them to visualize and gain full context and understanding of their attack surface. The visualization, analytics, and customized reporting empowers customers to make informed decisions and to automate workflows so they can ultimately achieve an optimized overall security posture.
(1) Gartner, “Guide to Cloud Security Concepts”, Patrick Hevesi, Richard Bartley, Dennis Xu, 21 September 2021
(2) Gartner, “2021 Strategic Roadmap for SASE Convergence”, Neil MacDonald, Nat Smith, Lawrence Orans, Joe Skorupa, 25 March 2021
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.

