We’ve all seen it: the infamous Google Maps car driving around the neighborhood, taking pictures for its maps. Google knows how important it is for drivers to visualize the roads. The same idea applies to your company’s cybersecurity—you must have an accurate view of your networks to see and defend against your biggest risks.
With a new vulnerability published every 17 minutes, knowing what’s lurking in your network in real-time is more critical than ever. Many breaches could be avoided if organizations had better visibility of their hybrid attack surface. By using a dynamic network security model to visualize and analyze their environment, security teams can more easily see gaps or potential risks in their environment, which allows them to make informed, proactive security decisions.
Create the framework
Research shows that organizations with more advanced cybersecurity practices take a risk-based approach. They regularly assess risk probabilities and impacts and work internally to prioritize and mitigate risks proactively. Solutions like continuous threat exposure management (CTEM) platforms help teams uncover threats quickly to stay ahead of cybercriminals – and be proactive, rather than reactive, regarding risks.
A critical part of a proactive cybersecurity strategy is building a comprehensive attack surface map of your networks. This provides visibility into your environment, so you understand things like vulnerability exposure to hackers or whether access compliance rules were violated. It also provides accurate details about traffic flow in and out of your network.
But, like road construction on Google Maps, to get the most accurate details, you also need to understand the surrounding context. Relevant information like threat intelligence (including exploitability) or the business context of the asset adds immense value to how you prioritize vulnerabilities. Using this information, you can better identify which assets may be at greatest risk to your organization.
Fill in the details
While having visibility into your network is a crucial step to securing it, sometimes, certain devices cannot be accessed or collected. When network devices in the path are missing, model accuracy declines. It may show areas inaccurately disconnected or provide incorrect paths, leaving critical risks missed. These gaps—or “missing next hops”—in the model are like Google Maps, leading you into a traffic jam because you didn’t realize there was an accident up ahead.
Thankfully, Google uses AI algorithms to provide real-time traffic for more accurate routes and travel times.
Similarly, AI can be used to enable full end-to-end visibility of your networks. Machine learning-assisted model exploration and completion create a dynamic security model that can be used as a single source of truth. With this knowledge, you can more accurately prioritize vulnerabilities in your environment, remediating those that are most critical first. You can also find and fix potential network issues before they impact the end-user experience. By looking at the risks that might be introduced when you implement a patch or other mitigation technique, you can ensure that no new vulnerabilities will be introduced.
Network modeling with Skybox
This is why Skybox built Model Booster. It was developed to improve our customers’ overall network visibility and connectivity so they stay better protected.
Often, despite best efforts, network models may have some missing hops. Model Booster creates an intelligent model to help with mapping and path analysis between locations where a model may have incomplete information. The model’s missing hop anomalies are resolved to provide a complete map for all locations, where they can successfully run access queries between critical locations.
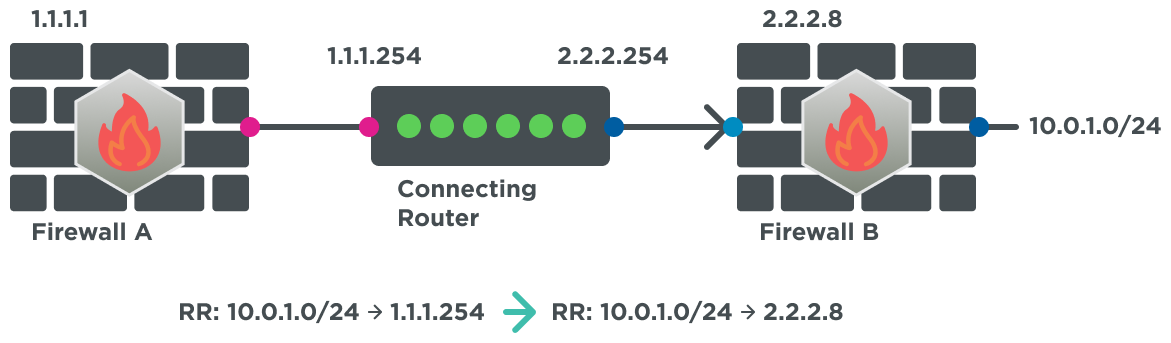
- Network visibility without Model Booster
For example, let’s say you are trying to complete the missing links between firewalls A and B. Model Booster can fill in these missing hops by extracting the data we know—primarily existing routing rules—and using it to calculate the addresses behind the interface (ABI). For example, if Firewall A and Firewall B are connected but the connecting router isn’t yet included in the model. However, Firewall A’s ABI contains Firewall B’s address and vice versa. As such, the firewalls can be connected via a virtual connecting router, thus completing the model.
- Network visibility with Model Booster
With this information, customers can bridge gaps and have a complete end-to-end model of their environment. With a richer set of paths to better analyze attack paths, they can make more accurate decisions for a risk-based approach to cybersecurity.
These Skybox products use Model Booster for complete end-to-end visualization of your hybrid attack surface:
Learn how Skybox’s dynamic security model, with Model Booster, can help you better protect your organization: