Security professionals are facing a perfect storm: an explosion of sophisticated threats, the complexities of managing sprawling networks, and the unrelenting pressure of continuous digital transformation.
Manual processes are taking up resource time, and associated costs are skyrocketing. Identifying roles and responsibilities across the attack surface, assessing access changes, and identifying the associated vulnerabilities can take many hours, even before implementation and verification of the change begins. The sheer volume of requests, rule changes, and regulatory requirements is overwhelming, and workloads are becoming unsustainable.
What if it was possible to liberate the team from routinely performing manual and time-consuming, attack surface, security policy, and vulnerability management tasks?
Automate network security policy management tasks
Skybox automation policies remove many time-consuming and costly manual tasks that preoccupy hard-pressed security and network teams, from assigning responsibility for assets across the attack surface to maintaining complex access security policies. The policies are also invaluable for informing vulnerability management prioritization, enabling the organization to automatically adjust risk scores and always maintain a “risk-aware” security posture.
Skybox’s automation policies run automatically to streamline and reduce workloads, making attack surface, security policy, and vulnerability management more effective. They also reduce costs in an increasingly expansive environment and reduce the risk of misconfigurations due to human error and associated compliance failure.
Automation policies leave the team free to focus on core business activities while routine, manual, and mundane tasks are automatically, securely, and safely executed without intervention.
Enhance attack surface management with automation policies
Automation policies included with the Skybox Cyber Asset Attack Surface Management (CAASM) solution, Model Explorer, enable the organization to enhance attack surface management by driving the oversight of assets and their associated metadata.
Using automation policies, organizations can set asset owners by policy to ensure the optimum allocation of responsibilities across the team. This can be further enhanced by setting asset metadata and key business attributes. For example, this enables the implementation of policies that automatically allocate an owner for all firewalls from a given vendor in a particular geographic region.
Automation policies are also a great way to automatically manage asset groups. For example, grouping important assets that may be subject to a specific operational process, such as compliance analysis.
Applying automation policies to attack surface management makes allocating responsibilities across the team and delegating task management easier. This enables robust governance and ultimately reduces the overall attack surface.
Use policy-driven security policy management to reduce costs and increase efficiency
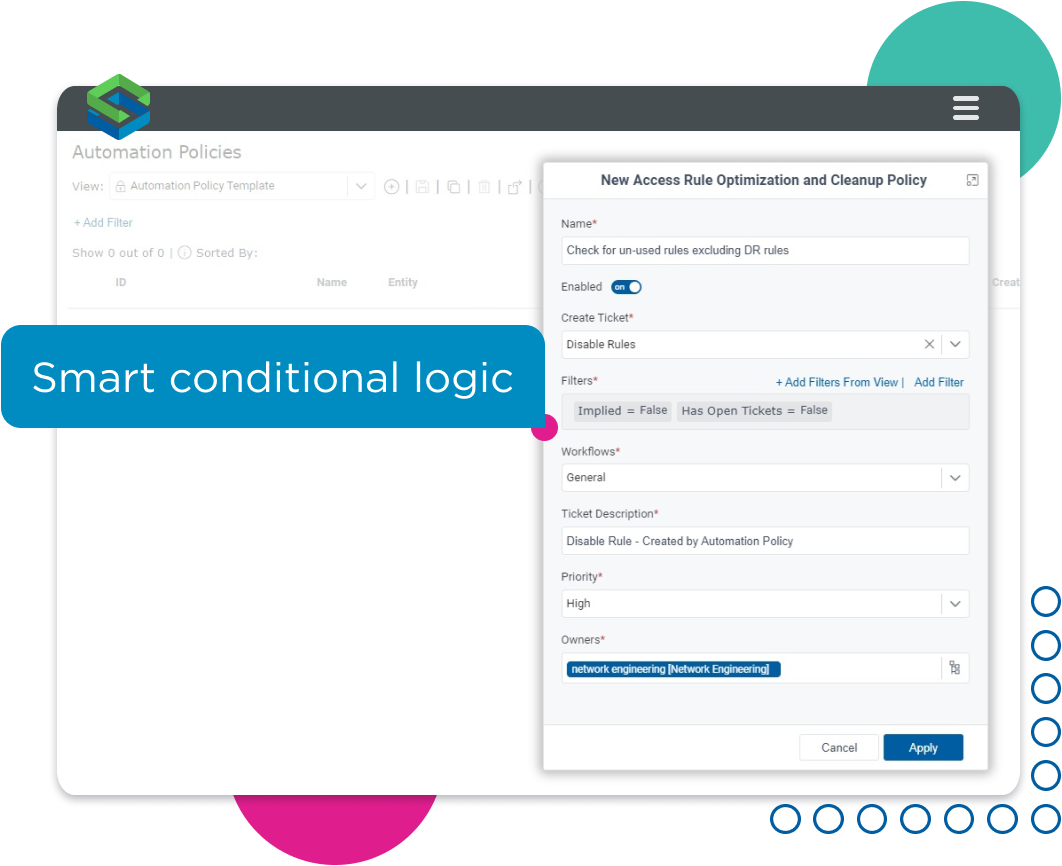
Security operations teams can rapidly build and deploy automation policies to improve and maintain security policy hygiene, optimize, and clean up firewall rule bases, and initiate change management workflows. For example, this policy-based approach makes it easy to automate the response to access rule compliance violations or access rule optimization. It works seamlessly with attack surface management automation policies.
The team can design policies based on a wide range of triggers, such as ownership details, change request status, priority level, and other metadata values.
For example, the organization can automatically clean up rule bases by disabling firewall rules that have been unused over a given time while exempting any rule tagged as “Disaster Recovery.” This smart conditional logic makes it easy to safely automate repetitive tasks accurately and securely.
Automatically disable un-used rules
Automate risk prioritization based on business impact
Skybox customers are already able to drive vulnerability management, using advanced multi-factor prioritization based on a combination of CVSS severity score, evidence of exploitability in the wild, asset importance, and insights into the extent to which an asset is accessible across the network.
Using automation policies, organizations can now set asset importance scores and Cyber Risk Quantification (CRQ) scores by policy. For example, organizations can use policies to identify assets by operating systems, group them, and assign an importance value. They can further specify that the importance score will change if the asset’s operating system changes.
Policies can also be used to create exceptions for vulnerabilities based on a trigger. For example, you can exclude specific development or pre-production assets from being included in the prioritization calculation.
Learn more about Cyber Risk Quantification:
Conclusion
Skybox’s automation policies provide a highly efficient solution for automating attack surface management, security policy management, and vulnerability management tasks and procedures.
These automation policies enable organizations to better manage their exposure across the attack surface, securely automate security policy changes, and respond immediately to the threats posed by vulnerabilities across the estate.
Using automation, Skybox enables organizations to respond more quickly to the rapidly changing technology landscape, maintain compliance with established industry best practices, reduce the risk that manual processes will introduce errors, and redeploy valuable technical resources to more skilled/important tasks.