“Gartner predicts that by 2026, organizations prioritizing their security investments based on a CTEM program will suffer two-thirds fewer breaches.”1
Effective exposure management not only identifies and prioritizes the most critical exposures; it also reduces noise and brings down the number of issues to remediate to a manageable level. The Continuous Threat Exposure Management (CTEM) model is a hot topic in the industry right now because it is seen as a solution to many of the challenges organizations face in mitigating cybersecurity risk.
Exposure management vs vulnerability management
Vulnerability management has been an established industry sector for many years. However, the legacy models for vulnerability management address only a small subset of the total risk exposure, informing the need for broader exposure management.
For example, a vulnerability on a server typically means a software or even a hardware defect that creates an opening an attacker could exploit to do something malicious. But when we look at the attack surface, we quickly realize there are a lot of potential exposures and risks that are not caused by vulnerabilities, for example a BYOD device that does not have endpoint security, or a misconfiguration of a firewall. These are not software defects, but they create huge openings. Exposure is a much wider term used to describe any risk, created in any way, which can be exploited.
Why continuous monitoring is crucial
The continuous nature of CTEM recognizes that the attack surface and threat landscape are changing all the time.
Modern organizations are agile – they continually add new servers, applications, and network paths, so the attack surface is ever evolving. In addition, the threat landscape is changing very rapidly, with around 30,000 new Common Vulnerabilities and Exposures (CVEs) published every year. It is no longer enough to perform vulnerability assessments periodically – monthly, or just once or twice a year. Annual analysis can result in reports with millions of entries that security and infrastructure teams are ill equipped to deal with.
Continuous exposure means we use a set of tools and capabilities to do threat analysis much more often. Effective exposure management means being able to do daily analysis and prioritization so that analysts can cut the noise and surface the top exposures they need to address.
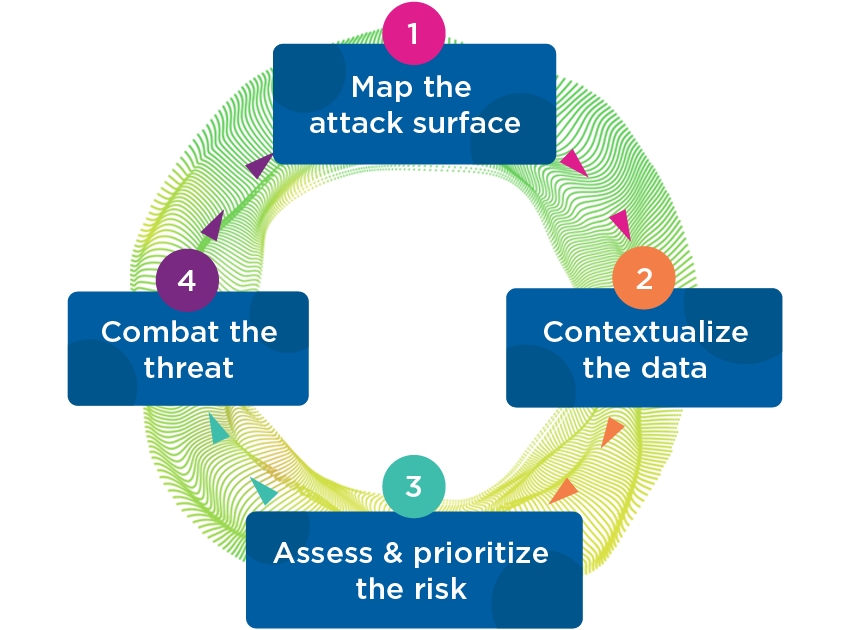
Successful CTEM programs are best understood as four distinct phases:
(1) Map the attack surface: this entails the scoping and definition of the assets which will be included in the program, with an inventory of all endpoints, servers, potentially network devices, cloud infrastructure and OT assets. It may also include user identities and applications. One challenge in this phase is to correctly classify and prioritize the assets. For example, asset importance is an extremely useful parameter to use when trying to decide the priority of exposures.
(2) Contextualize the data: involves a comprehensive discovery of exposures which is far broader than vulnerability scans. This should include looking at missing controls, misconfigurations, and testing infrastructure against security industry benchmarks that define best practices. In this phase, you typically find a large number of exposures and vulnerabilities. For example, we find an average of ten exposures per asset. In a large enterprise, the total number of exposures can seem overwhelming.
(3) Assess the risk: this critical phase can narrow down the number of occurrences detected from millions to double digits that must be addressed. Here, prioritization distills the overwhelming number of exposures down to the things most likely to cause harm. Properly executed, prioritization looks at the published severity of risks, CVSS score for an indication of the potential damage of exploitation of a vulnerability and how easy it would be to exploit it, and whether the vulnerability is theoretical or whether it is actually being exploited in the wild. Added to this, using an exploit probability score, asset importance, and network access analysis allows organizations to narrow down the number of severe and exploitable exposures on important assets. Validation checks can be used to ascertain whether the vulnerability or exposure can be used for malicious purposes on the specific asset. Attack path analysis is especially useful since it determines if the asset is actually exposed to the vulnerability, or if there is an access list, firewall rule or Intrusion Detection signature that mitigates the attack and reduces urgency.
(4) Combat the threat: During this phase, you mobilize a response and try to remove exposures from the list. Gartner makes the important observation that the most often neglected activities are prioritization and mobilization. Inadequate prioritization and remediation often have a lot to do with organizational structures – for example, security may come up with reports, and ‘throw them over the fence’ to the IT team to fix. So, mobilization is hard technically and organizationally. Remediation also requires integration into ITSM, with automation to streamline and automate cyclical processes. You also need the ability to report on the success of the program, with KPIs and SLA reports on how effective you were.
Holistic view of threat exposure management
Organizations evolving to adopt CTEM models should move to acquire the tools and capabilities to run these models effectively. They may potentially need to make organizational changes to implement programs – for example, joint security and infrastructure teams to implement them. In terms of tools, many probably already have some of the building blocks like security scans in place. What they need is additional tools like Skybox to analyze configurations, missing controls, and shadow IT, as well as the ability to aggregate the scans into one data model. This allows organizations to look at exposure holistically, mobilize to remediate exposure, and measure the success of the remediation.
Ready to put your CTEM program in motion? Get started with a special webinar: