Get back to the basics with OT network segmentation
OT cybersecurity people tend to focus on the “cool” hacker stuff they read about in the news. They’ll say they’re dealing with Log4j or trying to stop ransomware, but what they really need to focus on is the very basic element of network security appropriate network segmentation.
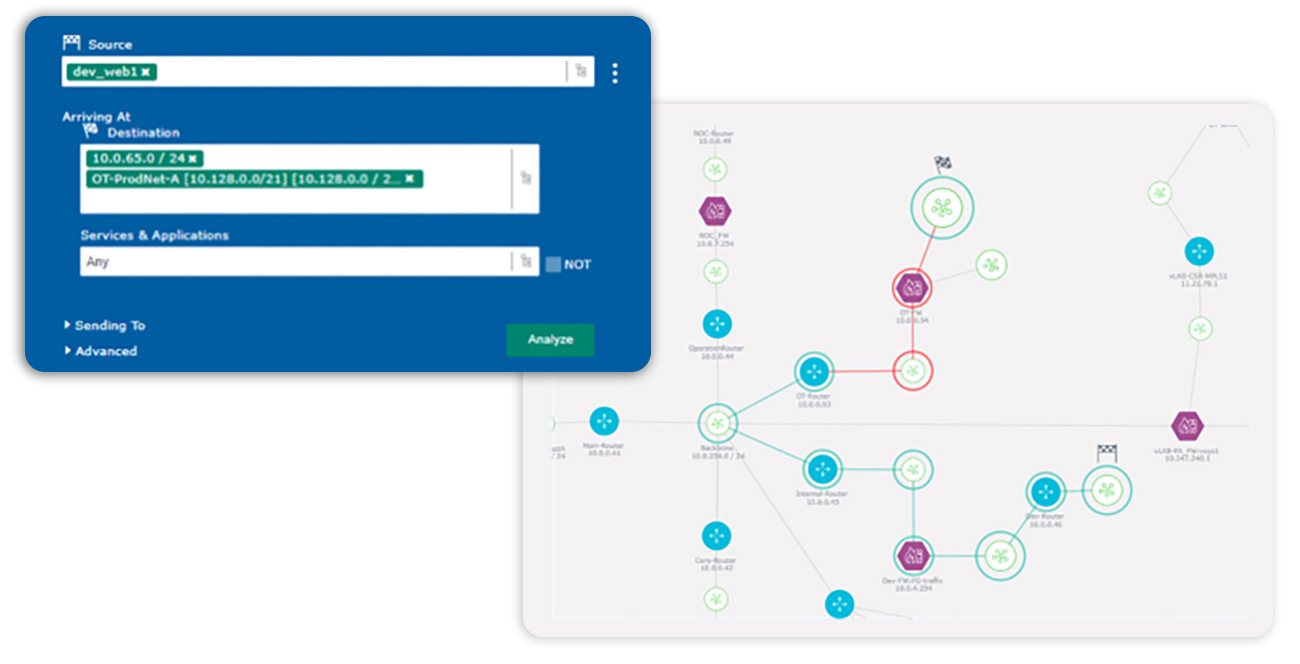
In some environments, OT network segmentation preventing networks from connecting and talking to one another based on security controls such as a firewall needs to be revalidated. There is a new set of issues in the world of the industrial Internet of Things (IoT), where there’s now a wireless architecture that OT security has never considered before.
OT devices are typically tiny equipment sensors sending tons of data wirelessly from a remote location to the front office so the company can gauge when something has failed. Because these sensors are built to communicate, not be secure, it is up to the company to make sure that the network they sit on is secure and compliant.
As the drive to introduce more ways to automate gains speed, OT security teams struggle to keep up. They don’t really know what they’re securing anymore, and how to secure it.
Why today’s OT environment requires a different approach
The OT space is about 10 years behind IT in terms of security. OT leaders are now finally starting to realize that they can’t control the security of the business 100 percent, which IT realized a while ago when they stopped trying to keep executives from getting a MacBook because of the burden of securing them.
Modern OT security teams deal with devices that speak a very specific protocol or language and they may not even have a firewall at the edge of the network where these devices or sensors reside. Putting up a firewall that stops these devices and sensors can stop business operations, so how do they secure them without introducing friction? These teams need to operate in real-time and very fast, otherwise the benefit of having timely data is lost. In some cases, not getting the necessary data can be catastrophic.
Blind spots across the IT and OT network increase cyber risk
Because there’s so much going on within the OT environment that a lot of security people don’t know about, it’s much easier for bad actors to gain access to the organization through OT networks. When I talk with OT teams, their chief worry is defending what they don’t know much about. They have a network connection they inherited or that someone else set up who is no longer there. They don’t know what to do with it and need to figure it out because they can’t stop that network from working. More importantly, they don’t know how that network connection fits into their OT network segmentation.
Get a comprehensive view of IT and OT assets and vulnerabilities in a single pane of glass.
OT security also needs to consider that OT networks, devices, and sensors are now connected to their IT network, so they must pivot from OT to IT and have access to any issues that moved to the IT network. If an issue occurs on an IT network, IT can just isolate devices or connections and put company employees to work on different workstations, but OT network access is business-critical because it involves an oil rig or water treatment plant that can’t be taken offline.
OT security professionals also worry about their own ability to deal with all of this. Smaller organizations, such as municipal utilities, may have only one person who handles OT security and doesn’t know who to turn to other than peers in the same industry. They don’t really have a support network. But that is starting to change and it’s another area where OT is catching up to IT, as IT has networks for sharing industry-specific processes with colleagues.
Perform an attack surface analysis
Assessing your attack surface entails determining which networks are talking to one another – across both the IT and OT environments.
A study done by a healthcare technology vendor reported that 92% of breaches or losses of information that happen in the healthcare industry could have been avoided by having appropriate segmentation. That number is so high because the organizations don’t have a good handle on how things are connected and talking to each other. Security professionals will say to me that their OT environment is secure and can’t be attacked because they only allow outbound connections to the Internet. I’ll ask them if they are sure they’re not allowing any inbound and they’ll say, ”Yes, we’re 100% sure, please check that.” But sure enough, I almost always find there’s an inbound connection or lateral access via IT connectivity set up.
Today’s hyper-connected networks need a more proactive approach to not only assess current network controls around segmentation, but to also shift left and assess network changes before they are implemented. By integrating into the Change Management process, you can both maintain compliance and stay compliant even in the face of rapid change. Continuous compliance is achievable by creating a network model, defining appropriate access, building policies to support the desired access controls, and running regular path analyses to validate the access policies. It’s critical to do these checks against a network model instead of the live network to avoid any potential network connectivity issues on central and field locations.
Context-driven network segmentation: device-independent access-analysis improves team efficiency
Running the business & HSE (Health, Safety, Environment) concerns will always take precedence over security, so if you are an OT security manager, you have to figure out how to make it work. Identify your attack surface first, and then have a conversation with your company’s leadership about what you have to do to secure the OT space – and still enable the business to run.
It’s important to understand what the business is doing and how you can keep it from being attacked. Simply go back to the basics. Set up and validate appropriate network segmentation, which allows you to gain the necessary attack surface visibility to minimize your attack surface area. Skybox can assist you with all of that with our network model approach and automated vulnerability management tools.