Today’s security professionals have a tough job. They face hundreds of new threats each week, struggle to get a budget for the required tools, and often work on small teams due to the ongoing shortage of cyber professionals.
To make matters worse, cybercriminals have become much faster at exploiting new CVEs. As noted in our 2024 Vulnerability and Threats Trends Report, the average time between the publication a CVE and the emergence of an exploit is 44 days. However, 25% of these CVEs were exploited on the same day they were published, and 75% were exploited within 19 days. That means security teams must act quickly when vulnerabilities appear in their environment.
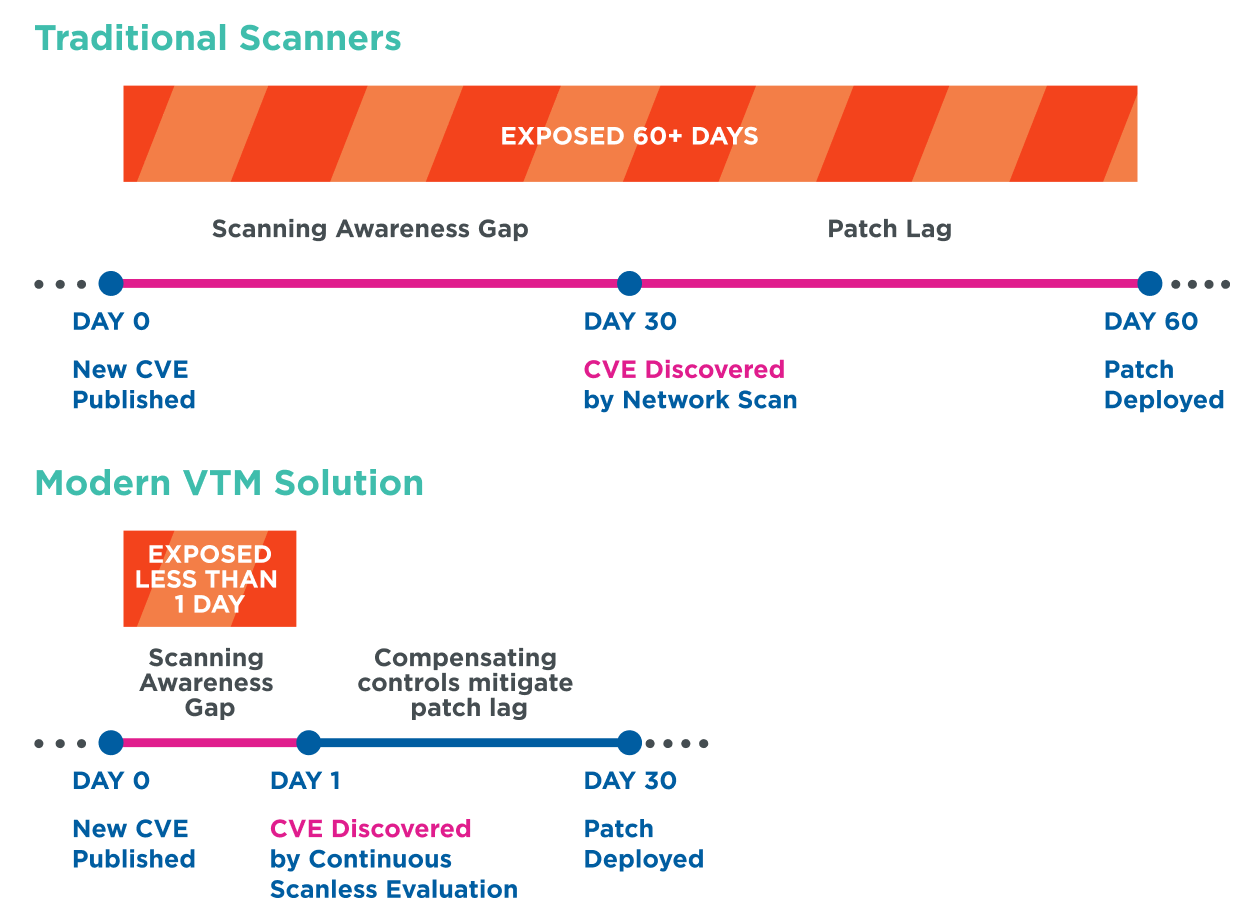
Prolonged timelines for scanning and remediation heighten risk
Unfortunately, most security teams only run periodic vulnerability scans; this leaves a long interval between scans and creates a substantial scanning awareness gap. Threats can go undetected for days, weeks, or even months, leaving cybercriminals a lot of time to lurk in your environment and cause significant damage. Even when a vulnerability is discovered, lengthy patch cycles for remediation subject organizations to an exposure gap of prolonged risk.
A new approach to vulnerability management
In today’s high-tech world, security teams can no longer rely on traditional vulnerability scanning methods alone to stay protected. This is why many organizations are looking for a modern vulnerability and threat management solution that continuously monitors their organization via scanless and agentless detection, provides visibility of their entire attack surface, and alerts them quickly of any new threats that enter their networks.
Then, to help mitigate risk until the next patch cycle, organizations must reduce risk by augmenting their patching strategy with additional security controls for more immediate protection. As detailed in our report, compensating security controls can include:
- Using an Intrusion Prevention Systems (IPS) signature to detect and block known attack patterns.
- Adding firewall rules to filter network traffic based on predefined rules.
- Segmenting networks (e.g., DMZ, internal, external) to limit lateral movement.
- Implementing host-based controls to monitor and block suspicious activity.
Vulnerability management has improved greatly in recent years. Still, with the high volume of new vulnerabilities, it’s more critical than ever that organizations are alerted quickly to threats and close the gaps rapidly. The war on cybercrime is never fully won – but if you outsmart them, you will stay ahead of threats and be better protected.