In the early days of computers, they were bulky, hooked up to local networks (so they required a physical on-site presence), and mostly used by research universities, government agencies, or large commercial businesses. As the years progressed, so did technology, with the rise of personal computers connecting more people and organizations worldwide. Alongside the exciting abilities and new realms of possibilities came a bigger challenge for IT teams – how to safeguard their networks. Internet connections allowed their networks to connect to the outside world, meaning organizations needed to better protect their people, physical assets, and data.
Enter the rise of security policy management.
What is Security Policy Management?
Network security policy management (often called security policy management, or SPM) helps organizations improve network visibility and ensure digital safety and integrity. Most policies are designed to secure an organization’s firewalls, networks, and assets against unapproved access, use, changes, or destruction. An internal team, often consisting of networking and security members, builds policies that describe parameters in detail, such as the network architecture and who or what is allowed to access which resources.
While writing these policies may be complex and time-consuming, having a strong security policy in place helps minimize risks and reduce the likelihood of a breach. The process usually encompasses activities such as:
- Design security policies outlining the protocols for accessing and utilizing the organization’s networks and assets.
- Establish strict access control measures to ensure that only authorized individuals access sensitive information and critical infrastructure.
- Inventory all digital assets to ensure that these assets are protected from unauthorized changes, theft, or destruction.
- Create an incident response plan, so you know what steps to take if a security breach occurs.
- Ensure compliance by continuously monitoring that you’re meeting established regulatory compliance standards relevant to your industry.
Creating and maintaining rules around security policies helps keep everyone in the organization working towards a common goal, as security threats and the business evolves. However, with the rapid change of the cyberthreat landscape, it’s critical to follow some best practices when creating a program.
How to build an effective Security Policy Management program
However, there are ways to alleviate some of those challenges when building out your policies. Here are the three things to consider:
- Increase visibility: Aggregate data and share across teams to remove silos and enable complete visibility of your environment. Visibility provides the context for analyzing rules, optimizing security policies, and increasing efficiency.
- Embrace automation: Automate change management workflows, such as provisioning and validating firewall rules, to improve business agility and reduce manual errors. By expediting these processes, you also free up staff time for more crucial priorities.
- Manage compliance: Continually review firewall rule configurations to ensure you meet compliance requirements. This makes keeping up with complex, changing regulations easier and ensures you are audit-ready.
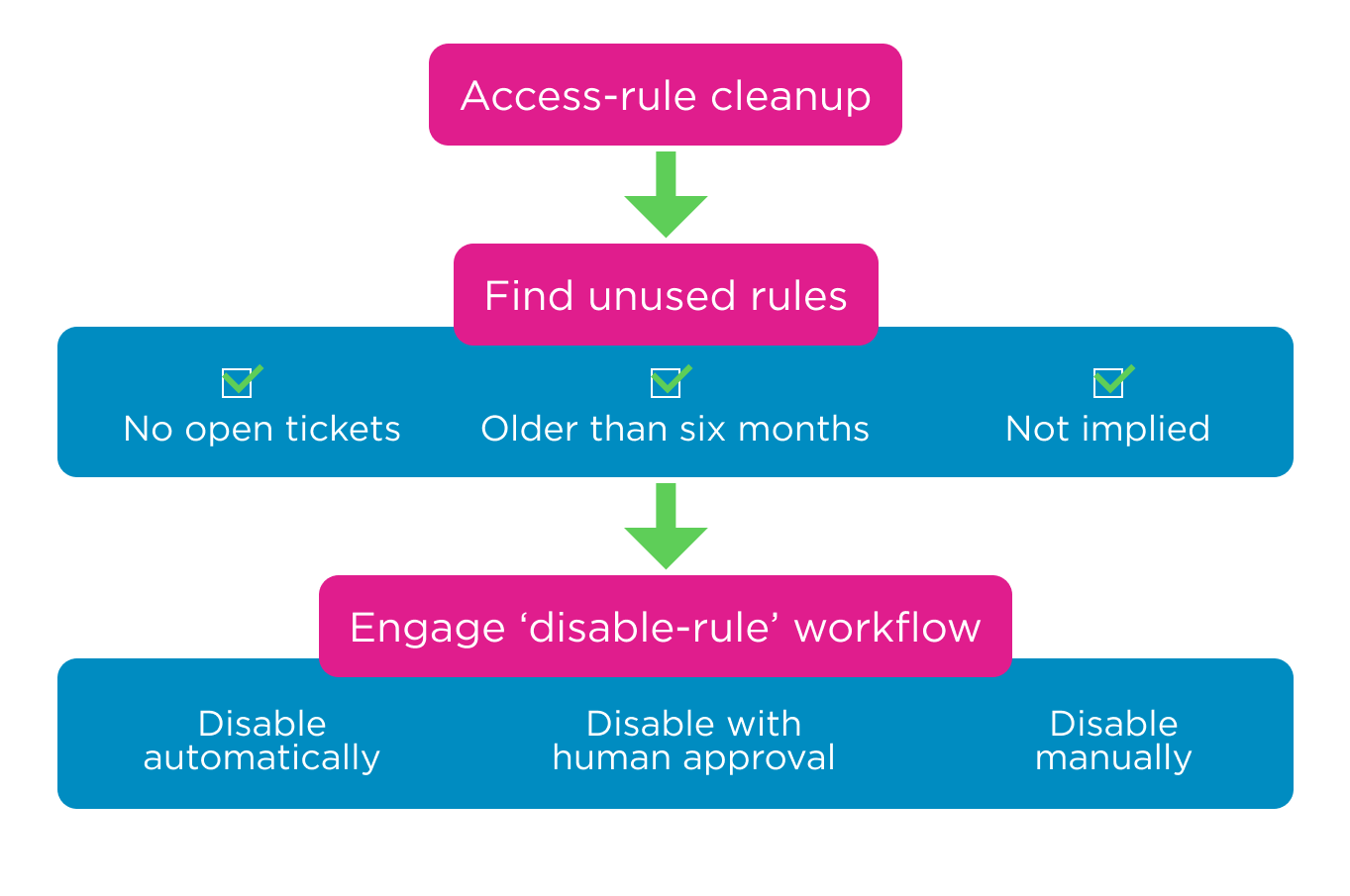
Designing a successful security policy management program not only helps ensure the integrity and safety of the network, but if done properly, it will reduce teams’ workload through streamlined and consistent processes. With the complexities and size of most organizations’ networks today, it is imperative add a Network Security Management tool.
Selecting a Network Security Management tool
As organizations expand their teams and technology, it’s essential to embrace the technologies that streamline tasks and optimize operations. Adding a Network Security Management tool helps ensure efficiency, security, and sustained progress while proactively addressing vulnerabilities.
But how do you find the right tool?
A Network Security Management tool that provides smart automation will help you reduce manual errors and save on costs.
In addition to automation, a Network Security Management tool helps you tackle other challenges, such as visibility or compliance. Some other things to consider may be:
- Asset Inventory – Do you have an inventory of all attackable assets for continuous attack surface management?
- Visibility— Do you get a network topology map with a detailed view of your hybrid network?
- Risk Assessments – Do you see potential risks for proposed network changes before making the change?
- Compliance—Does this tool offer out-of-the-box compliance reports and maintain continuous compliance to ensure you’re maintaining regulatory requirements?
- Integrations— Does your solution ingest and normalize data from your current IT and security tools to provide a single source of truth?
- Flexibility and Customization—Does the tool allow you to build custom reports, dashboards, or searches for your business requirements?
While implementing a security policy program is an easy decision, the process of creating and maintaining it is often much more challenging. With Skybox’s Network Security Policy Management solution, you manage your firewall and network policies all from one platform and continually enforce your network security policy. Skybox gives unparalleled visibility into your network through our dynamic network model, helps you optimize and clean up rule bases to maximize firewall efficiency, and identifies potential vulnerabilities a proposed change could introduce.