Streamline audits by maintaining and documenting security policy hygiene across on-premises, hybrid, and cloud resources.
Reduce the attack surface by identifying and removing unnecessary or risky access.
Ensure all rules respond to an identified business need.
Improve network device performance by reordering rulesets.
Accelerate incident response with accurate firewall data reporting.
By identifying and troubleshooting unused, shadowed, or outdated rules, you can prioritize rule optimization and address misconfigurations, aligning security policies more effectively with business objectives to manage risk.
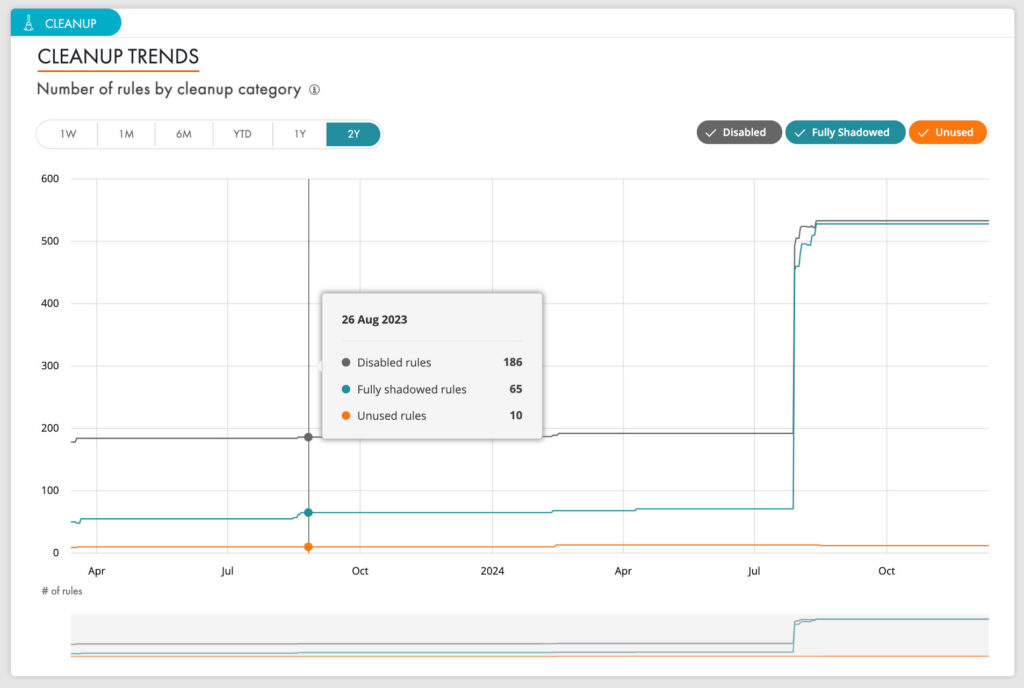
By tightening rules, you can enforce the principle of least privilege consistently across network devices and control network access more precisely.
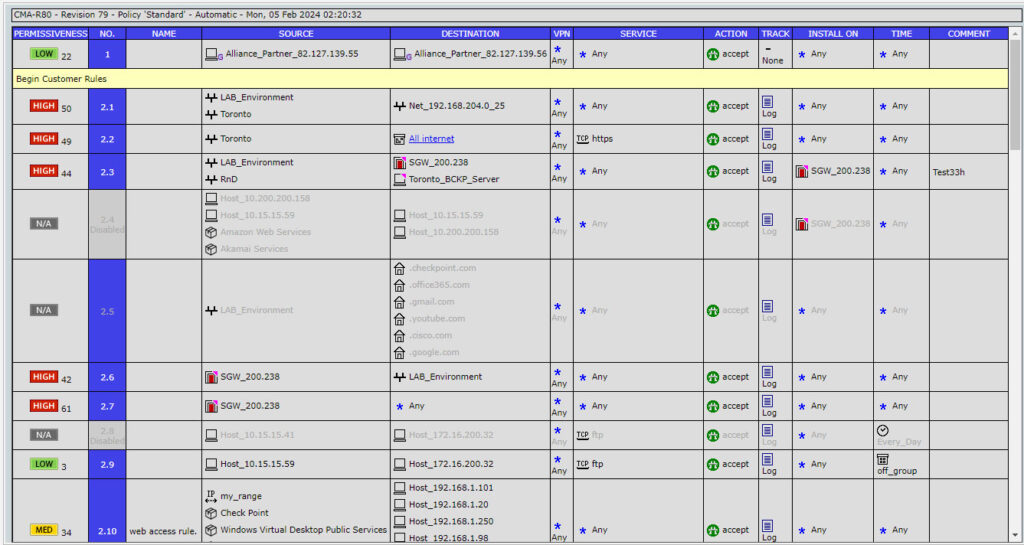
Streamlining and reordering firewall rulesets within your firewall policy improves overall network speed and performance, while effective change management in policy management helps mitigate transmission bottlenecks and enhances cybersecurity.
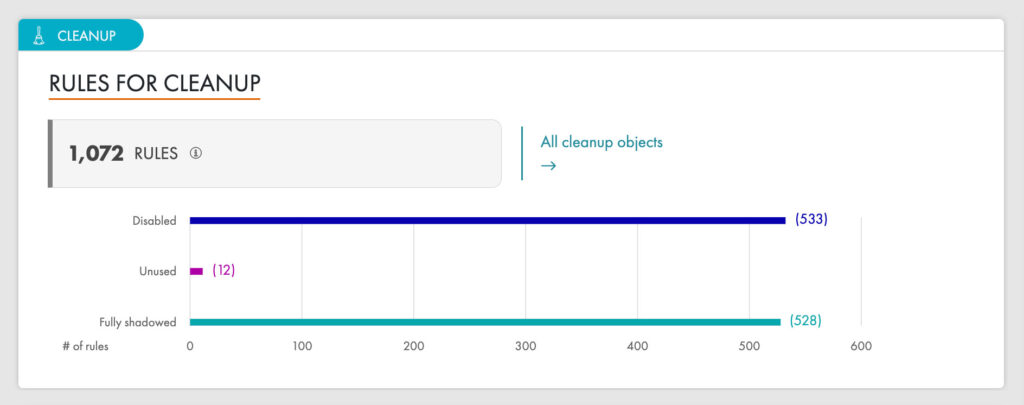
By establishing consistent security policies and continuously monitoring for violations, you can strengthen your security posture, enhance firewall security, and reduce audit times, all while mitigating cyber threats and optimizing bandwidth.
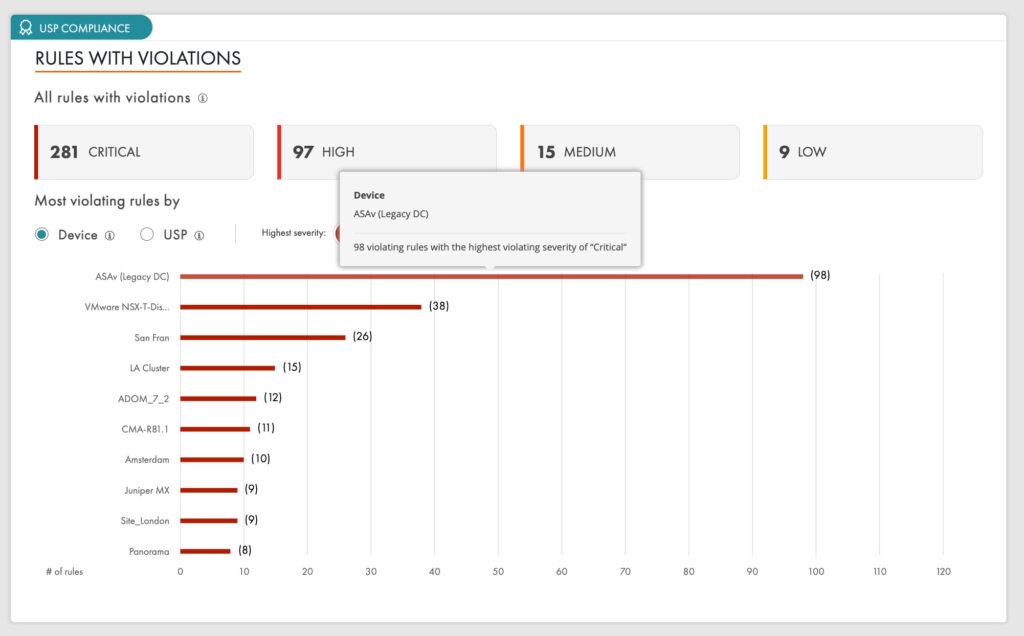
With end-to-end network visibility and accurate firewall data, your security teams can optimize policies, analyze traffic patterns, and enhance segmentation and authentication, leading to improved metrics like Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
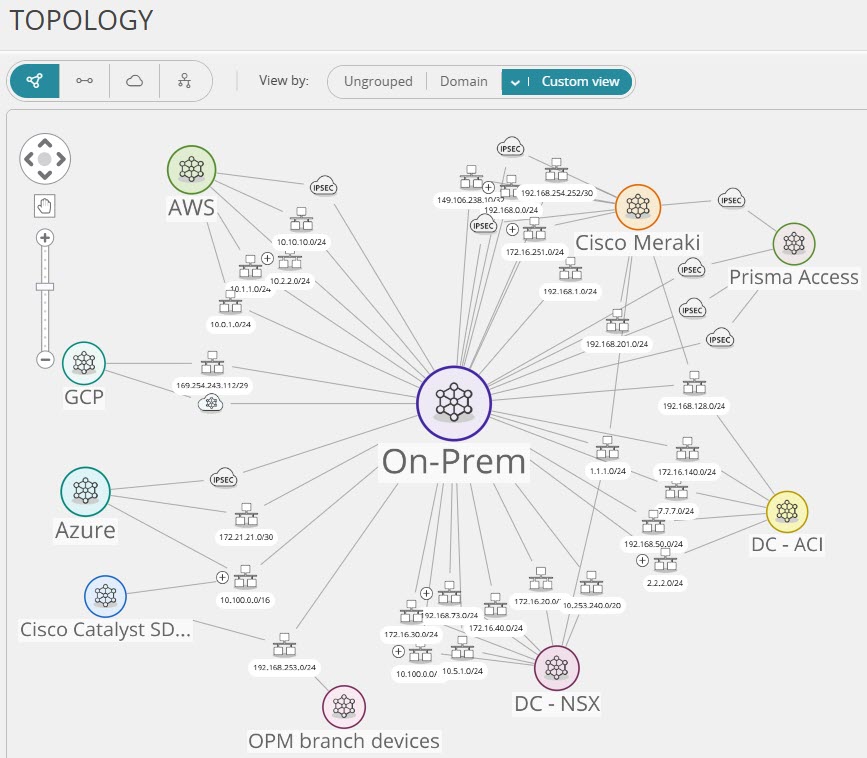
Learn more about how Tufin optimizes network security policies and cloud security to reduce firewall complexity and address potential threats while enhancing overall network performance.

Elevate your network security and cloud security operations with Tufin's product tiers. Addressing the most challenging use cases, from segmentation insights to enterprise-wide orchestration and automation, experience a holistic approach to network security policy management.